Backbone - A backbone is a major network connection that provides the main pathway through a network, much like an interstate highway does. When referring to the Internet Backbone, we are talking about a number of high speed fiber optic connections that connect major networks together. together.
Bandwidth - The term bandwidth refers to the amount of data that a given network connection can transmit. One can think of this like the size of a plumbing pipe - the wider the pipe, the more water can be carried at a time. As an example, 10base-T has a bandwidth of 10mbps.
BGP (Border Gateway Protocol) - BGP is used to connect autonomous systems, which are very large "collections" of networks. As opposed to routing protocols such as EIGRP and OSPF, BGP is an exterior routing protocol. BGP is not used to find a specific network instead, it's used to find the autonomous system where that given network can be found. A good way to look at it is that networks are contained in Autonomous Systems and BGP helps you find the AS where a given network is found. Routing protocols such as OSPF and EIGRP take it from there. Introduction to BGP
Binary - Refers to the ‘language’ computers speak. Binary code (or machine language) consists only of zeroes and ones (ie a choice is either on or off), called bits. Letters and other information have a specific binary representation made up of up to 8 bits (one byte). speak. Binary code (or machine language) consists only of zeroes and ones (ie a choice is either on or off), called bits. Letters and other information have a specific binary representation made up of up to 8 bits (one byte).
BIND (Berkeley Internet Name Domain) - Previously known as Berkeley Internet Name Daemon, BIND is the most widely used DNS server on Linux and Unix systems. For this reason, it is the most widely used DNS server on the internet. BIND was developed by the University of California Berkeley.
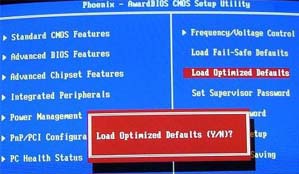 BIOS - BIOS stands for Basic Input/Output System and is software that manages hardware and allows the operating system to talk to the various components. The BIOS is also responsible for allowing you to control your computer's hardware settings, for booting up the machine when you turn on the power or hit the reset button and various other system functions. The BIOS software lives on a ROM IC on the motherboard known as a Complementary Metal Oxide Semiconductor(CMOS). People often incorrectly refer to the BIOS setup utility as CMOS, however, CMOS is the name of the physical location that the BIOS settings are stored in. The term BIOS is typically used to refer to the system BIOS, however, various other components such as video adapters and hard drives can have their own BIOSes hardwired to them. BIOS - BIOS stands for Basic Input/Output System and is software that manages hardware and allows the operating system to talk to the various components. The BIOS is also responsible for allowing you to control your computer's hardware settings, for booting up the machine when you turn on the power or hit the reset button and various other system functions. The BIOS software lives on a ROM IC on the motherboard known as a Complementary Metal Oxide Semiconductor(CMOS). People often incorrectly refer to the BIOS setup utility as CMOS, however, CMOS is the name of the physical location that the BIOS settings are stored in. The term BIOS is typically used to refer to the system BIOS, however, various other components such as video adapters and hard drives can have their own BIOSes hardwired to them.
BIT - A binary digit which is the smallest piece of information that a computer can hold. A bit is always one of two values, written as 1 or 0, corresponding to the on or off state of a digital switch or the high or low of electrical impulses. Single characters of information are represented by a combination of bits called bytes. For personal computers, a byte equals eight bits.
Bluetooth - Bluetooth (IEEE 802.15.1), originally developed by Ericsson and later formalized by the Bluetooth Special Interest Group (SIG), is a specification for wireless personal area networks that facilitates the exchange of data between electronic devices, such as mobile phones, PDAs, laptops, personal computers, printers and digital cameras. The devices, containing a low-cost transceiver, connect to each other using a short range radio frequency (2.45 gHz) of up to 328 feet. Each Bluetooth enabled device is assigned a unique 48-bit address and a 24-bit class identifier. The class identifier provides information as to the nature of the device (phone, PC, etc.) and is transmitted to other devices performing an inquiry.
BMP - Bitmap files are the default bitmapped images used in on Windows operating systems and are a Microsoft proprietary file format. The Windows "Paint" program is designed to work with BMP files. BMP files can support up to 16.7M colors. The BMP format supports RGB, indexed-colour, greyscale, and bitmap color modes.
 BNC (Bayonet Neill Concelman) - Sometimes incorrectly referred to as a "British Naval Connector", this connector named after its inventor has found uses with both broadcast television equipment and computer networks. Nowadays, it is most commonly seen as the connector found on coaxial cable used in homes. With regards to networking, this connector was used on early 10Base-2 (Thinnet) Ethernet networks. It has a center pin connected to the center cable conductor and a metal tube connected to the outer cable shield. A rotating ring outside the tube locks the cable to the female connector. BNC (Bayonet Neill Concelman) - Sometimes incorrectly referred to as a "British Naval Connector", this connector named after its inventor has found uses with both broadcast television equipment and computer networks. Nowadays, it is most commonly seen as the connector found on coaxial cable used in homes. With regards to networking, this connector was used on early 10Base-2 (Thinnet) Ethernet networks. It has a center pin connected to the center cable conductor and a metal tube connected to the outer cable shield. A rotating ring outside the tube locks the cable to the female connector.
Bootcamps - A certification bootcamp is a training school offering an intesive program whereby candidates can prepare for certification exams in short amounts of time. Typically, the candidate will travel away from home and stay at the training facility or in a hotel nearby. The length of the camps can vary from a few days to a couple of weeks. Criticisms of bootcamps include the fact that they promote memorization rather than learning, are very expensive, and often use illegal training materials such as braindumps and real exam questions.
Braindumps - Traditionally, the term 'braindump' referred to a list of exam questions posted by someone immediately after taking the exam. As time has passed, it is also used to denote real exam questions that are sold or posted on internet sites. These questions are usually acquired from bad testing centers, or by a person taking screenshots of the exam questions with a tiny camera. Posting braindumps is a violation of the Non-disclosure agreement that you sign before taking the exam. Using braindumps is cheating, and is completely unethical. Braindumps and Real Exam Questions
Bridge - Functions the same as a repeater, but can also divide a network in order to reduce traffic problems. A bridge can also connect unlike network segments (ie. token ring and ethernet). Bridges create routing tables based on the source address. If the bridge can't find the source address it will forward the packets to all segments. Bridging methods: - Transparent - Only one bridge is used.
- Source-Route - Bridging address tables are stored on each PC on the network
- Spanning Tree - Prevents looping where there exists more than one path between segments
Broadcast – traffic sent out from a network node that will reach every other node on the subnet / broadcast domain because the message is sent with the intent of reaching all nodes. The network node that is sending the traffic will use the broadcast address for that subnet and every device in that broadcast domain will receive the broadcast information. Generally the broadcast address is the last IP address of that segment. As an example, in the IP address range of 192.168.0.0 this broadcast address would be 192.168.255.255 and the traffic would reach all available nodes on the subnet. Additionally 255.255.255.255 could be used which is the broadcast address of the zero network (0.0.0.0). Internet Protocol standards outline that the zero network stands for the local network so only those node on the local network would hear the broadcast traffic across the 255.255.255.255 address.
BTX - A standard proposed by Intel, the BTX form factor provides better airflow and cooling, specifically the thermal unit which blows hot air from the CPU directly out of the case. At this time, it is unknown if this form factor will become the standard replacing the ATX form factor, however, it is being used on many new computers.
Bus - A collection of wires through which data is transmitted from one part of a computer to another. You can think of a bus as a highway on which data travels within a computer. There are busses both within the CPU and connecting it to external memory and peripheral devices. The bus width (ie, the number of parallel connectors) is one factor limiting a computer's performance.
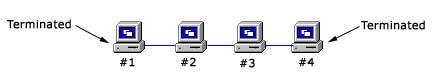
Bus Topology - A bus network topology is one in which all nodes (workstations and other network devices) are connected to a main cable known as "the bus" which is terminated at both ends. Bus networks are not commonly used anymore - Ethernet 10Base-2 and 10Base-5 networks are bus networks. The Bus Topology
Byte - A byte is a series of 8 bits used as a unit of storage measurement in computers. Large amounts of memory are indicated in terms of kilobytes (1,024 bytes), megabytes (1,048,576 bytes), and gigabytes (1,073,741,824 bytes). Byte Converter.
 CAPTCHA - Developed by Carnegie Mellon University, CAPTCHA stands for "Completely Automated Public Turing test to tell Computers and Humans Apart". This system was developed to prevent internet bots used by spammers to automatically fill out forms on web sites and submit them. On a form, CAPTCHA displays a series of distorted letters and numbers that must be correctly entered in order to submit the form. Recently, spambots have begun using character recognition software that is able to bypass this in many cases. CAPTCHA - Developed by Carnegie Mellon University, CAPTCHA stands for "Completely Automated Public Turing test to tell Computers and Humans Apart". This system was developed to prevent internet bots used by spammers to automatically fill out forms on web sites and submit them. On a form, CAPTCHA displays a series of distorted letters and numbers that must be correctly entered in order to submit the form. Recently, spambots have begun using character recognition software that is able to bypass this in many cases.
CBT (Computer Based Training) - Traditionally, computer based training is composed of self-paced tutorials, tests, and simulations that a student can study on their computer. In the certification industry, most CBT products consist of classroom-style videos sold on DVDs. The benefits of CBTs over classroom training is the much lower price, the ability to take your study materials anywhere, and the ability to skip around or repeat portions of the video as necessary.
CGI (Common Gateway Interface) - A Common Gateway Interface (CGI) is a standard protocol for interfacing external application software with a web server. This allows the server to pass requests from a client web browser to the external application. The web server can then return the output from the application to the web browser. On the web server, there will usually be a cgibin directory where PERL and other CGI applications are stored. to the external application. The web server can then return the output from the application to the web browser. On the web server, there will usually be a cgibin directory where PERL and other CGI applications are stored.
CHAP (Challenge Handshake Authentication Protocol) - A type of authentication protocol used on PPP connections. CHAP uses a 3-way handshake in which the authentication agent sends the client program a key to be used to encrypt the user name and password. CHAP not only requires the client to authenticate itself at startup time, but sends challenges at regular intervals to make sure the client hasn't been replaced by an intruder, for instance by switching phone lines. For more detailed information, click here.
CIDR (Classless Inter-Domain Routing) - Classless Interdomain Routing (CIDR) was introduced to improve both address space utilization and routing scalability in the Internet. It was needed because of the rapid growth of the Internet and growth of the IP routing tables held in the Internet routers. CIDR moves way from the traditional IP classes (Class A, Class B, Class C, and so on). In CIDR, an IP network is represented by a prefix, which is an IP address and some indication of the length of the mask. Length means the number of left-most contiguous mask bits that are set to one. So network 172.16.0.0 255.255.0.0 can be represented as 172.16.0.0/16. CIDR also depicts a more hierarchical Internet architecture, where each domain takes its IP addresses from a higher level. This allows for the summarization of the domains to be done at the higher level. For example, if an ISP owns network 172.16.0.0/16, then the ISP can offer 172.16.1.0/24, 172.16.2.0/24,and so on to customers. Yet, when advertising to other providers, the ISP only needs to advertise 172.16.0.0/16.
Circuit Switching - In circuit switching, a dedicated path is built between the source and destination, and the packets will all be sent over this dedicated path. If this sounds like a telephone call, you're right! A phone call is a great example of circuit switching. On a Cisco router, ISDN is a circuit-switching technology. Introduction to WAN Technologies call, you're right! A phone call is a great example of circuit switching. On a Cisco router, ISDN is a circuit-switching technology. Introduction to WAN Technologies
Cisco Networking Academy - The Cisco Networking Academy Program is a comprehensive e-learning program that provides students with the Internet technology skills essential in a global economy. The Networking Academy delivers web-based content, online assessment, student performance tracking, hands-on labs, instructor training and support, and preparation for industry standard certifications. Launched in October 1997, the Networking Academy has spread to more than 150 countries. Since its inception, over 1.6 Million students have enrolled at more than 10,000 Academies located in high schools, technical schools, colleges, universities, and community-based organizations. Cisco Networking Academy Program
Clustering - Clustering is the use of multiple computers and storage devices that are virtually combined together to create what seems to be a single system. Clustering is often used to increase a system's availability, performance, and for load balancing on highly-trafficked Web sites or database servers.
 Coaxial - This cable, often referred to as "coax", is mainly known for its use with cable television systems. It was once used on early Ethernet bus networks (10Base-2), however, it has been replaced for this application by twisted pair and fiber optic cabling. More recently, this cable has proven itself useful for broadband internet connections because of its ability to transmit large amounts of data over long distances. This cable is made of a central conductive core that is wrapped in an insulator and then a second conductive layer. These three layers are then typically wrapped in an outer insulating layer. Coaxial - This cable, often referred to as "coax", is mainly known for its use with cable television systems. It was once used on early Ethernet bus networks (10Base-2), however, it has been replaced for this application by twisted pair and fiber optic cabling. More recently, this cable has proven itself useful for broadband internet connections because of its ability to transmit large amounts of data over long distances. This cable is made of a central conductive core that is wrapped in an insulator and then a second conductive layer. These three layers are then typically wrapped in an outer insulating layer.
CompactFlash - CompactFlash is the oldest and largest of the flash card types and is based on a simplified PCMCIA bus. CF cards come in CF I and CF II sizes, the latter being thicker. Like all other flash cards, the CompactFlash cards are solid state, although some manufacturers have turned this form factor into microdrives which are minature hard drives. These drives have platters and heads just like a regular hard drive. The two types look identical, however, microdrives can use too much power for some devices, but are less expensive.
Convergence – Convergence is achieved when all of the available topology information from routing devices have been passed along to all of the other deceives in totality and all when the information gathered is not in a contradiction state to any other router's informed topology information. When all of the network routing devices "agree" on what the network topology looks like it is said to have full convergence.
Cookie - Cookies are unencrypted text files stored on the client computer that store information about the user for use on a web site. They are commonly used to customize pages for you based on your browser type, or other information and preferences that you may have provided the Web site. Most browsers will accept cookies by default, however, the security settings can be changed to reject them. If this is done, some web pages will lose functionality or not work correctly. An expiration date can be set in a cookie. If no expiration is set, the cookie will expire when the browser is closed. A single domain is restricted to only setting 20 cookies and each cookie can be a maximum of 4KB in order to prevent client machines from being inundated with cookies and filling up hard drive space.
 CPU (Central Processing Unit) - A CPU, also known as a processor or microprocessor, can be thought of as the brains of a computer system and is responsible for executing software commands and performing calculation functions. Microprocessors CPU (Central Processing Unit) - A CPU, also known as a processor or microprocessor, can be thought of as the brains of a computer system and is responsible for executing software commands and performing calculation functions. Microprocessors
Cryptography - Cryptography is typically concerned with the processes of scrambling ordinary text (known as plain text or clear text) into encrypted text (Ciphertext) at the sender’s end of a connection, and decrypting the encrypted text back into clear text at the receiver’s end. This is accomplished using a specific algorithm and a secret key. It is used to protect e-mail messages, credit card information, and other forms of electronic data. Common types of cryptography include Public-key Cryptography and Symmetric-key Cryptography.
CSMA/CD (Carrier Sense Multiple Access with Collision Detection - In the early days of ethernet, when two hosts would send packets at the same time, a collision would occur. A standard had to be created that would have the hosts follow rules relating to when they could send data and when they could not. This standard is Carrier Sense Multiple Access with Collision Detection, referred to as CSMA/CD. CSMA/CD forces computers to “listen” to the wire before sending in order to make sure that no other host on the wire is sending. If a collision is detected, both of the senders will send a jam signal over the Ethernet. This jam signal indicates to all other devices on the Ethernet segment that there has been a collision, and they should not send data onto the wire.
How Ethernet CSMA/CD Works
CSS (Cascading Style Sheets) - CSS provides an easier solution to site updates by storing formatting paramaters for all of the text, layout, and other elements in a single master file. The .css file is denoted in the HEAD section of the HTML document and individual settings are called using the CLASS attribute with HTML tags. CSS Tutorials
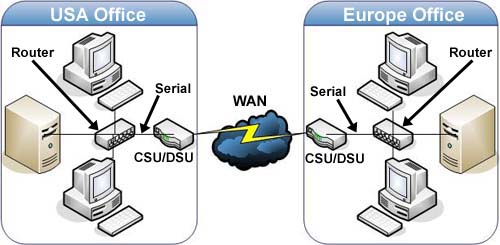
CSU/DSU (Channel Service Unit/Data Service Unit) - This is a piece of equipment that connects a leased line from the telephone company to the customer's equipment (such as a router). Although CSU/DSU's look similar to modems, they are not modems, and they don't modulate or demodulate between analog and digital. All they really do is interface between a 56K, T1, or T3 line and serial interface (typically a V.35 connector) that connects to the router. Many newer routers have 56K or T1 CSU/DSUs built into them.
|
Daemon - A daemon is more or less the Unix/Linux equivalent of a service in Windows. It is an automated background process that manages resources, processes, etc. The names of most daemons end in the letter "d" such as inetd, ftpd, and httpd.
 DB Connector - Describes a series of port connectors for connecting devices to a computer. It gets its name because the connectors have a definite shape like a capital D (also could be called a trapezoid with rounded angles). Typically these come with 9, 15, 25, 50, or 68 pins and can be male or female depending on the cable's function. DB Connector - Describes a series of port connectors for connecting devices to a computer. It gets its name because the connectors have a definite shape like a capital D (also could be called a trapezoid with rounded angles). Typically these come with 9, 15, 25, 50, or 68 pins and can be male or female depending on the cable's function.
 DDR SDRAM - Double-Data-Rate Synchronous Dynamic Random Access Memory is a type of memory integrated circuit used in modern computers. It achieves greater bandwidth than ordinary SDRAM by transferring data on both the rising and falling edges of the clock signal (double pumped). This effectively nearly doubles the transfer rate without increasing the frequency of the front side bus. Thus a 100 MHz DDR system has an effective clock rate of 200 MHz when compared to equivalent SDR SDRAM, the “SDR” being a retroactive designation. With data being transferred 8 bytes at a time DDR RAM gives a transfer rate of (memory bus clock rate) × 2 (for dual rate) × 8 (number of bytes transferred). Thus with a bus frequency of 100 MHz, DDR-SDRAM gives a max transfer rate of 1600 MB/s. The DDR SDRAM standard is evolving, from DDR to DDR2 to DDR-3. DDR SDRAM - Double-Data-Rate Synchronous Dynamic Random Access Memory is a type of memory integrated circuit used in modern computers. It achieves greater bandwidth than ordinary SDRAM by transferring data on both the rising and falling edges of the clock signal (double pumped). This effectively nearly doubles the transfer rate without increasing the frequency of the front side bus. Thus a 100 MHz DDR system has an effective clock rate of 200 MHz when compared to equivalent SDR SDRAM, the “SDR” being a retroactive designation. With data being transferred 8 bytes at a time DDR RAM gives a transfer rate of (memory bus clock rate) × 2 (for dual rate) × 8 (number of bytes transferred). Thus with a bus frequency of 100 MHz, DDR-SDRAM gives a max transfer rate of 1600 MB/s. The DDR SDRAM standard is evolving, from DDR to DDR2 to DDR-3.
Default Gateway - A default gateway is a node on a computer network that serves as an access point to another network such as the internet. This node is usually a router.
Demarcation Point – is the point of operational and administrative control change in a network. One example of this is the Main Distribution Frame (MDF) point in a facility. This is where the wire distribution frame for connecting equipment inside a facility to cables and subscriber carrier equipment outside of the facility occurs and this is considered a demarcation point of the operational control of the internal systems where it changes over to the control of the external presence.
DES (Data Encryption Standard) - Created in the 1970's, DES was a widely-used method of data encryption using a private (secret) key that was judged so difficult to break by the US government that it was restricted for exportation to other countries. There are 72,000,000,000,000,000 (72 quadrillion) or more possible encryption keys that can be used. For each given message, the key is chosen at random from among this enormous number of keys. By current standards, DES is considered to be slow and offers weak encryption. EAS replaced DES as the standard for the U.S. Government.
DHCP (Dynamic Host Configuration Protocol) - DHCP is responsible for automatically assigning IP addresses to computers on a network. When a client is configured to receive an IP address automatically, It will send out a broadcast to the DHCP server requesting an address. The server will then issue a "lease" and assign it to that client. DHCP can also assign other network parameters such as subnet masks and default gateways. DHCP makes network configuration easier and helps prevent the assignment of duplicate addresses.
Introduction to DHCP
DHCP and RARP
Distance-vector Routing Protocols – are one of the two main classes of routing protocols used in packet switching networks and includes Routing Information Protocol (RIP) and Interior Gateway Routing Protocol (IGRP). uses distance as one factor and the vector as the other to determine against the known routing tables to deliver data to source and destination locations. Routers using the distance-vector routing protocol will update other routers of topology changes periodically when a change is detected in the topology of a network. and includes Routing Information Protocol (RIP) and Interior Gateway Routing Protocol (IGRP). uses distance as one factor and the vector as the other to determine against the known routing tables to deliver data to source and destination locations. Routers using the distance-vector routing protocol will update other routers of topology changes periodically when a change is detected in the topology of a network.
DSSS (Direct Sequence Spread-Spectrum) - One of two types of spread-spectrum radio technology used in wireless LAN (WLAN) transmissions. To increase a data signal’s resistance to interference, the signal at the sending station is combined with a higher-rate bit sequence that spreads the user data in frequency by a factor equal to the spreading ratio. It phase-modulates a sine wave pseudorandomly with a continuous string of pseudonoise code symbols called "chips", each of which has a much shorter duration than an information bit. That is, each information bit is modulated by a sequence of much faster chips. Therefore, the chip rate is much higher than the information signal bit rate. DSSS uses a signal structure in which the sequence of chips produced by the transmitter is known a priori by the receiver. The receiver can then use the same PN sequence to counteract the effect of the PN sequence on the received signal in order to reconstruct the information signal. See also FHSS.
DHTML (Dynamic HTML) - A loosely-used term refering to the combination of JavaScript and Cascading Style Sheets to introduce interactivity to web pages. DHTML is less commonly used now that programming languages such as PHP and ASP have taken over some of its capabilities.
DIMM - Short for Dual In-line Memory Module, a small circuit board that holds memory chips. A single in-line memory module (SIMM) has a 32-bit path to the memory chips whereas a DIMM has 64-bit path. Because the Pentium processor requires a 64-bit path to memory, you need to install SIMMs two at a time. With DIMMs, you can install memory one DIMM at a time.
DLL (Dynamic Link Library) - DLL files are used in conjunction with Microsoft operating systems and contain executable functions or data that is used by applications at run-time. These binary files can be shared by multiple applications at once in some instances, others are only used with one specific application. When an application utilizes a .dll file, the OS maps the DLL into the process' address space. When the application is terminated, the link to the .dll file ends as well.
DMA - Direct Memory Access - DMA channels allow hardware devices (like sound cards or keyboards) to access the main memory without involving the CPU. This frees up CPU resources for other tasks.
DNS (Domain Name System) - DNS is an Internet and networking service that translates domain names into IP addresses. The internet is based on numerical IP addresses, but we use domain names because they are easier to remember. DNS is the service that looks up the IP address for a domain name allowing a connection to be made. This process is very similar to calling information. You call them with a name, they check their database and give you the phone number.
Domain Name System Overview
DNS, DDNS, and DHCP
Configuring Windows XP Professional as a DNS Client
Domain Controller - On a Windows network, a Domain Controller is a server that stores the central database of users, accounts, security information, and other network resources. This central database was known as NT Lan Manager (or NTLM) in Windows NT. Newer Microsoft server operating systems such as Windows 2003 use a database called Active Directory. Each person who uses a computer that is a member of the domain, receives his or her own unique account, or user name. This account can then be assigned access to resources within the domain. Domain controllers are the servers that manage all security-related aspects of a user and domain interactions, centralising security and administration.
Domain Name - See also Windows Domain. The most common type of domain names are hostnames that provide more memorable names to stand in for numeric IP addresses. They allow for any service to move to a different location in the topology of the Internet (or an intranet), which would then have a different IP address. By making possible the use of unique alphabetical addresses instead of numeric ones, domain names allow Internet users to easily find and communicate with web sites and other server-based services. As an example, it is much easier to remember the domain name "techtutorials.net" than it's corresponding IP address of 206.67.48.220. The internet uses DNS to make these translations between domain names and the associated IP address.
Domain Naming Master - With regards to Active Directory, the Domain Naming Master FSMO controls the addition of Domains in a forest. This DC is the only one that can add or remove a domain from the directory.
DoS (Denial of Service) - A DoS attack is a common type of attack in which false requests to a server overload it to the point that it is unable to handle valid requests. There are several different types of DoS attacks including Syn Flooding and Ping Flooding.
DRAM - DRAM stand for Dynamic Random Access Memory and uses capacitors instead of transistors and switches. It needs to be constantly refreshed. DRAM is slower than SRAM, but is more commonly used for computers' main memory. Specialized types of DRAM (such as EDO memory) have been developed to work with today's faster processors.
DRDRAM - (See RDRAM)
DSL (Digital Subscriber Line) - A technology enabling high speed data transfer over ordinary copper telephone lines that has become a common broadband internet connection in many homes. In addition to much faster speeds, DSL has been a remarkable improvement over dial-up because it allows simultaneous voice and data communications. xDSL refers to different variations of DSL, such as ADSL, HDSL, iDSL and RADSL (ADSL is the most common). DSL's biggest competitor is broadband cable providers. lines that has become a common broadband internet connection in many homes. In addition to much faster speeds, DSL has been a remarkable improvement over dial-up because it allows simultaneous voice and data communications. xDSL refers to different variations of DSL, such as ADSL, HDSL, iDSL and RADSL (ADSL is the most common). DSL's biggest competitor is broadband cable providers.
|
EAP (Extensible Authentication Protocol) - EAP is an extension to the Point-to-Point Protocol (PPP) was developed in response to an increasing demand to provide an industry-standard architecture for support of additional authentication methods within PPP. EAP is an authentication framework, not a specific authentication mechanism that is typically used on wireless networks . It provides some common functions and negotiation of authentication methods, called EAP methods. There are roughly 40 different methods defined. Commonly used methods capable of operating in wireless networks include EAP-TLS, EAP-SIM, EAP-AKA, PEAP, LEAP and EAP-TTLS. When EAP is invoked by an 802.1X enabled Network Access Server (NAS) device such as an 802.11 Wireless Access Point, modern EAP methods can provide a secure authentication mechanism and negotiate a secure Pair-wise Master Key (PMK) between the client and NAS. The PMK can then be used for the wireless encryption session which uses TKIP or CCMP (based on AES) encryption. Strong EAP types such as those based on certificates offer better security against brute-force or dictionary attacks and password guessing than password-based authentication protocols, such as CHAP or MS-CHAP. . It provides some common functions and negotiation of authentication methods, called EAP methods. There are roughly 40 different methods defined. Commonly used methods capable of operating in wireless networks include EAP-TLS, EAP-SIM, EAP-AKA, PEAP, LEAP and EAP-TTLS. When EAP is invoked by an 802.1X enabled Network Access Server (NAS) device such as an 802.11 Wireless Access Point, modern EAP methods can provide a secure authentication mechanism and negotiate a secure Pair-wise Master Key (PMK) between the client and NAS. The PMK can then be used for the wireless encryption session which uses TKIP or CCMP (based on AES) encryption. Strong EAP types such as those based on certificates offer better security against brute-force or dictionary attacks and password guessing than password-based authentication protocols, such as CHAP or MS-CHAP.
Echo - Occurs when portions of a transmission are repeated. Echoes can occur during many locations along the route. Splices and improper termination in the network can cause a transmission packet to reflect back to the source, which causes the sound of an echo. To correct for echo, network technicians can introduce an echo canceller to the network design. This will cancel out the energy being reflected.
EDI (Electronic Data Interchange) - EDI is the computer-to-computer exchange of business information using a public standard. EDI is a central part of e-commerce, because it enables companies to exchange business information electronically much faster, cheaper and more accurately than is possible using paper-based systems. The parties who exchange EDI transmissions are referred to as trading partners.
EIGRP (Enhanced Interior Gateway Routing Protocol) - EIGRP is a Cisco proprietary distance vector routing protocol, with optimizations to minimize both the routing instability incurred after topology changes, as well as the use of bandwidth and processing power in the router. For EIGRP, separate routing tables are maintained for IP, IPX and AppleTalk protocols. However, routing update information is still forwarded with a single protocol.
Enhanced Interior Gateway Routing Protocol (EIGRP)
EIGRP Dual Queries, SIA, and Stub Routers
 EISA (Extended Industry Standard Architecture) - EISA is a bus standard for IBM compatible computers. It was announced in late 1988 by PC clone vendors as a counter to IBM's use of its proprietary MicroChannel Architecture (MCA) in its PS/2 series. EISA extends the ISA bus architecture to 32 bits and allows more than one CPU to share the bus. The bus mastering support is also enhanced to provide access to 4 GB of memory. Unlike MCA, EISA can accept older XT and ISA boards — the lines and slots for EISA are a superset of ISA. Although somewhat inferior to MCA, EISA was much favoured by manufacturers due to the proprietary nature of MCA, and even IBM produced some machines supporting it. It was somewhat expensive to implement (though not as much as MCA), so it never became particularly popular in desktop PCs. However, it was reasonably successful in the server market, as it was better suited to bandwidth-intensive tasks (such as disk access and networking). Most EISA cards produced were either SCSI or network cards. EISA is not commonly seen anymore. EISA (Extended Industry Standard Architecture) - EISA is a bus standard for IBM compatible computers. It was announced in late 1988 by PC clone vendors as a counter to IBM's use of its proprietary MicroChannel Architecture (MCA) in its PS/2 series. EISA extends the ISA bus architecture to 32 bits and allows more than one CPU to share the bus. The bus mastering support is also enhanced to provide access to 4 GB of memory. Unlike MCA, EISA can accept older XT and ISA boards — the lines and slots for EISA are a superset of ISA. Although somewhat inferior to MCA, EISA was much favoured by manufacturers due to the proprietary nature of MCA, and even IBM produced some machines supporting it. It was somewhat expensive to implement (though not as much as MCA), so it never became particularly popular in desktop PCs. However, it was reasonably successful in the server market, as it was better suited to bandwidth-intensive tasks (such as disk access and networking). Most EISA cards produced were either SCSI or network cards. EISA is not commonly seen anymore.
Ethernet - Created by Xerox, Intel , and DEC in 1976, Ethernet has been standardized as IEEE 802.3. Ethernet is a large and diverse family of frame-based computer networking technologies for local area networks (LANs). It defines a number of wiring and signaling standards for the physical layer, two means of network access at the Media Access Control (MAC)/Data Link Layer, and a common addressing format. The original implementations of Ethernet used coaxial cable in a bus topology. The current star-topology, twisted pair or fiber optic wiring form has become the most common LAN technology in use, largely replacing competing LAN standards such as token ring, FDDI, and ARCNET. There are many different forms of Ethernet currently in use varying from 10Base-T which utilizes twisted pair wiring at speeds of 10mbps, to 1000Base-LX which operates at speeds up to 1gbps over fiber optic cabling. Ethernet Technologies , and DEC in 1976, Ethernet has been standardized as IEEE 802.3. Ethernet is a large and diverse family of frame-based computer networking technologies for local area networks (LANs). It defines a number of wiring and signaling standards for the physical layer, two means of network access at the Media Access Control (MAC)/Data Link Layer, and a common addressing format. The original implementations of Ethernet used coaxial cable in a bus topology. The current star-topology, twisted pair or fiber optic wiring form has become the most common LAN technology in use, largely replacing competing LAN standards such as token ring, FDDI, and ARCNET. There are many different forms of Ethernet currently in use varying from 10Base-T which utilizes twisted pair wiring at speeds of 10mbps, to 1000Base-LX which operates at speeds up to 1gbps over fiber optic cabling. Ethernet Technologies
|
FAT (File Allocation Table) - The FAT file system has its origins in the late 1970s and early 1980s and was the file system supported by the Microsoft MS-DOS operating system. It was originally developed as a simple file system suitable for floppy disk drives less than 500K in size. Over time it has been enhanced to support larger and larger media. Currently there are three FAT file system types: FAT12, FAT16 and FAT32. The basic difference in these FAT sub types, and the reason for the names, is the size, in bits, of the entries in the actual FAT structure on the disk. There are 12 bits in a FAT12 FAT entry, 16 bits in a FAT16 FAT entry and 32 bits in a FAT32 FAT entry.
Fault Tolerance - describes a computer system or component designed so that, in the event that a component fails, a backup component or procedure can immediately take its place with no loss of service. Fault tolerance can be provided with software, or embedded in hardware, or provided by some combination. Some levels of RAID are an example of fault tolerance.
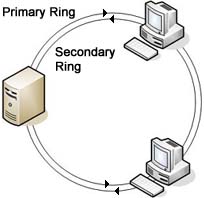 FDDI - Stands for Fiber Distrubuted Data Interface which is a set of ANSI protocols which specifies a 100-Mbps token-passing, dual-ring LAN using fiber-optic cable. FDDI uses dual-ring architecture with traffic on each ring flowing in opposite directions (called counter-rotating). The dual rings consist of a primary and a secondary ring. During normal operation, the primary ring is used for data transmission, and the secondary ring remains idle. FDDI defines two types of optical fiber: single-mode and multimode. A mode is a ray of light that enters the fiber at a particular angle. Multimode fiber uses LED as the light-generating device, while single-mode fiber generally uses lasers. FDDI allows 2 km between stations using multimode fiber, and even longer distances using a single mode. An extension to FDDI, called FDDI-2, supports the transmission of voice and video information as well as data. Another variation of FDDI, called FDDI Full Duplex Technology (FFDT) uses the same network infrastructure but can potentially support data rates up to 200 Mbps. More information FDDI - Stands for Fiber Distrubuted Data Interface which is a set of ANSI protocols which specifies a 100-Mbps token-passing, dual-ring LAN using fiber-optic cable. FDDI uses dual-ring architecture with traffic on each ring flowing in opposite directions (called counter-rotating). The dual rings consist of a primary and a secondary ring. During normal operation, the primary ring is used for data transmission, and the secondary ring remains idle. FDDI defines two types of optical fiber: single-mode and multimode. A mode is a ray of light that enters the fiber at a particular angle. Multimode fiber uses LED as the light-generating device, while single-mode fiber generally uses lasers. FDDI allows 2 km between stations using multimode fiber, and even longer distances using a single mode. An extension to FDDI, called FDDI-2, supports the transmission of voice and video information as well as data. Another variation of FDDI, called FDDI Full Duplex Technology (FFDT) uses the same network infrastructure but can potentially support data rates up to 200 Mbps. More information
FHSS (Frequency-Hopping Spread Spectrum) - Frequency-hopping spread spectrum (FHSS) is a method of transmitting radio signals by rapidly switching a carrier among many frequency channels, using a pseudorandom sequence known to both transmitter and receiver. Multiple systems can operate using the same sequence, however, the chance of collisions increases as more and more users use the same sequence.
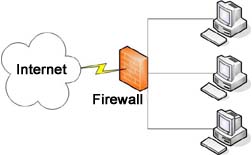 Firewall - Either a hardware or software entity (or a combination of both) that protects a network by stopping network traffic from passing through it. In most cases, a firewall is placed on the network to allow all internal traffic to leave the network (email to the outside world, web access, etc.), but stop unwanted traffic from the outside world from entering the internal network. This is achieved by granting and denying access to various ports. Firewall - Either a hardware or software entity (or a combination of both) that protects a network by stopping network traffic from passing through it. In most cases, a firewall is placed on the network to allow all internal traffic to leave the network (email to the outside world, web access, etc.), but stop unwanted traffic from the outside world from entering the internal network. This is achieved by granting and denying access to various ports.
 Firewire (IEEE-1394) - A very fast external bus similar to USB that supports data transfer rates of up to 400 Mbps. Firewire was developed by Apple and falls under the IEEE 1394 standard. Also known as the High Performance Serial Bus, firewire can connect up to 63 devices in a tree-like daisy chain configuration. It supports plug-and-play and peer-to-peer communication between computers Firewire (IEEE-1394) - A very fast external bus similar to USB that supports data transfer rates of up to 400 Mbps. Firewire was developed by Apple and falls under the IEEE 1394 standard. Also known as the High Performance Serial Bus, firewire can connect up to 63 devices in a tree-like daisy chain configuration. It supports plug-and-play and peer-to-peer communication between computers . .
Flash - Developed by Macromedia and now owned by Adobe, Flash is used to create vector graphics-based animation programs that are small enough to stream across a normal modem connection. In order for a web browser to display Flash animation, a plug-in must be installed on the user's system.
Adobe's Official Site
 Flash Drives - Flash drives offer advantages over other portable storage devices and are partially responsible for the disappearance of floppy and ZIP disk technologies. They are more compact, generally faster, hold more data, and are more reliable due to both their lack of moving parts (solid state), and their more durable design. These types of drives use the USB mass storage standard, and therefore, can be used with Linux, Mac OS X, Unix, and Windows. The drive is simply plugged into the computer's USB port and it registers as removable storage in My Computer (Windows). Newer computer systems will also allow these drives to be selected as the boot device which can be useful for storing certain utilities and troubleshooting tools. In Windows Vista, the ReadyBoost feature allows use of a flash drive to supplement system memory. At the time of this writing there are flash drives with a storage capacity of up to 64 gigabytes. Flash Drives - Flash drives offer advantages over other portable storage devices and are partially responsible for the disappearance of floppy and ZIP disk technologies. They are more compact, generally faster, hold more data, and are more reliable due to both their lack of moving parts (solid state), and their more durable design. These types of drives use the USB mass storage standard, and therefore, can be used with Linux, Mac OS X, Unix, and Windows. The drive is simply plugged into the computer's USB port and it registers as removable storage in My Computer (Windows). Newer computer systems will also allow these drives to be selected as the boot device which can be useful for storing certain utilities and troubleshooting tools. In Windows Vista, the ReadyBoost feature allows use of a flash drive to supplement system memory. At the time of this writing there are flash drives with a storage capacity of up to 64 gigabytes.
Frame Relay - Frame Relay is the successor to X.25 and is a high speed WAN protocol operating at the physical and data link layers. Frame Relay is a packet switching technology that was originally designed to run on ISDN interfaces, but can now run on T-carrier systems. This technology operates at speeds in between the range of 56 Kbps to 45 Mbps (T-3), and can transmit voice and data. To some degree, this technology is being displaced by broadband cable and DSL technologies.
Frame Relay Technology Overview
FSMO Roles (Flexible Single Master Operation Roles) - To prevent update conflicts, Active Directory performs updates to certain objects in a single-master fashion. In a single-master network model, only one domain controller in an Active Directory handles updates. Windows 2000 Active Directory extends the single-master model to include multiple roles and the ability to transfer roles to any DC. Since an Active Directory role is not bound to a single DC, it is referred to as a Flexible Single Master Operation role. There are five FSMO roles which are Schema Master, Domain Naming Master, RID Master, PDC Emulator, and Infrastructure Daemon.
Introduction to Active Directory
FTP (File Transfer Protocol) - FTP is a member of the Internet Protocol suite and the primary method of transferring files over the Internet. An FTP client can upload or download files from an FTP server regardless of the operating systems involved. As a user, you can use FTP with a simple command line interface or with a commercial program that offers a graphical user interface such as WS_FTP or Cute FTP. Two transfer modes are used in FTP. ASCII and BINARY. ASCII mode is used for the transfer of files consisting of plain text while the BINARY mode is used all types of files not consisting of plain text (such as sound, video, executables, images etc). Failure to upload files in the proper format can corrupt them. interface or with a commercial program that offers a graphical user interface such as WS_FTP or Cute FTP. Two transfer modes are used in FTP. ASCII and BINARY. ASCII mode is used for the transfer of files consisting of plain text while the BINARY mode is used all types of files not consisting of plain text (such as sound, video, executables, images etc). Failure to upload files in the proper format can corrupt them.
Ghost - Ghost is a disk cloning program, originally produced by Binary Research, but purchased by Symantec in 1998. The Ghost program created the market for disk-cloning software. The name Ghost originated as an acronym for "General Hardware-Oriented Software Transfer".
Symantec official site
 Ghosting - Ghosting is a condition where the image prints properly, but a much lighter copy of the image also prints elsewhere. This can be due to a problem with the power outlet that is supplying power to the printer. Check the power outlet by plugging in a different printer to see if the same results occur. Ghosting can also be caused when consumable printer parts, such as the drum or imaging kit, are near the end of their life. All of the consumable parts in a printer are rated for a certain number of pages. Once a printer gets near that number, you'll need to replace those parts to eliminate ghosting. Ghosting - Ghosting is a condition where the image prints properly, but a much lighter copy of the image also prints elsewhere. This can be due to a problem with the power outlet that is supplying power to the printer. Check the power outlet by plugging in a different printer to see if the same results occur. Ghosting can also be caused when consumable printer parts, such as the drum or imaging kit, are near the end of their life. All of the consumable parts in a printer are rated for a certain number of pages. Once a printer gets near that number, you'll need to replace those parts to eliminate ghosting.
Printer Troubleshooting Guide
GIF (Graphics Interchange Format) - A GIF is a palette based image format used for web site graphics and images. It can have a maximum of 256 colors, or 8 bits, chosen from a total of 16.7 Million, or 24 bits. GIFs can also be animated (GIF89a format only) and support transparency. The GIF89a standard also supports interlacing.
GIMP (GNU Image Manipulation Program) - GIMP is an open source application similar to Photoshop for creating and manipulating graphic images. Originally designed for Linux and UNIX-based operating systems, GIMP now runs on Windows and Mac operating systems as well. It is distributed under licensing terms defined by the GNU project. GIMP is typically one of the optional applications that come in any large Linux package such as those distributed by Debian and Red Hat. You can also download it directly from the GIMP web site.
GNOME (GNU Network Object Model Environment) - GNOME (pronounced guh-nome) is part of the GNU project and part of the or open source movement. The GNOME project provides two things: The GNOME desktop environment, an intuitive and attractive desktop for users, and the GNOME development platform, an extensive framework for building applications that integrate into the rest of the desktop. GNOME is the official desktop of the GNU project and is available for most Linux and Unix operating systems. GNOME official site
GNU (GNU's Not Unix) - The GNU (pronounced guh-new) Project was launched in 1984 to develop a complete UNIX-like operating system which is free software: the GNU system. Variants of the GNU operating system, which use the kernel called Linux, are now widely used; though these systems are often referred to as “Linux”, they are more accurately called GNU/Linux systems. GNU was created by the Free Software Foundation and distributes it's software under the GNU Public License (GPL). GNU official site called Linux, are now widely used; though these systems are often referred to as “Linux”, they are more accurately called GNU/Linux systems. GNU was created by the Free Software Foundation and distributes it's software under the GNU Public License (GPL). GNU official site
GPL (Gnu Not Unix Public License) - GPL is a licensing method commonly used in the Linux world. When a programmer decides to place his work under the GPL, they have an obligation to freely give this software, without charges and to publish all of the source code. Only shipping, handling and media can be billed. Whenever the author makes updates to the software, it must be publicly published along with the updated code.
GNU Official site
 GPS (Global Positioning System) - GPS refers to satellite-based radio positioning systems that provides one's exact location anywhere on or near the surface of the Earth. The NAVSTAR system, operated by the US Department of Defense, was the first GPS system widely available to civilian users who now use it for navigation purposes. Many corporations, such as UPS, use this technology for inventory tracking. GPS is made possible by a series of at least 24 geosynchronous satellites. GPS (Global Positioning System) - GPS refers to satellite-based radio positioning systems that provides one's exact location anywhere on or near the surface of the Earth. The NAVSTAR system, operated by the US Department of Defense, was the first GPS system widely available to civilian users who now use it for navigation purposes. Many corporations, such as UPS, use this technology for inventory tracking. GPS is made possible by a series of at least 24 geosynchronous satellites.
Group Policy - Group Policy and the Active Directory services infrastructure in Windows Server 2000 and 2003 enable IT administrators to automate one-to-many management of users and computers . By editing Group Policy Objects (GPOs) which contain policy settings and targeting the GPO at the intended machines or users, specific configuration parameters can be managed centrally. In this way, potentially thousands of machines or users can be updated via a simple change to a single GPO. . By editing Group Policy Objects (GPOs) which contain policy settings and targeting the GPO at the intended machines or users, specific configuration parameters can be managed centrally. In this way, potentially thousands of machines or users can be updated via a simple change to a single GPO.
GUI (Graphical User Interface) - A GUI (pronounced goo-ee) is a software front-end on a computer meant to provide an attractive and easy to use interface between a computer user and application. This is accomplished via the use of an external pointing device, such as a mouse, and a graphical interface consisting of icons, folders, menus, etc., as opposed to a command-line interface. The first GUI was created by Xerox in the late 70's and later became part of Mac and Windows operating systems.
|
HDLC (High-level Data Link Control) - Encapsulates the data during transmission and is a link layer protocol which is also the default Cisco encapsulation protocol for synchronous serial links. HDLC is supposed to be an open standard, but Cisco's version is proprietary, meaning it can only function with Cisco routers.
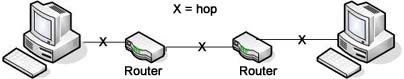
Hop - An intermediate connection in a string of connections linking two network devices. On the Internet, for example, most data packets need to go through quite a few routers before they reach their final destination. Each time the packet hits another network device, a hop occurs. You can see how many hops it takes to get to another Internet host by using the PATHPING or traceroute utilities.
HTML (HyperText Markup Language) - HTML is a basic language used to write web pages. HTML is a markup language and not a full-blown programming language. HTML is parsed by your web browser when a web page downloads and consists of tags (commands) which control the page layout, formatting of text, locations of images, etc. is a basic language used to write web pages. HTML is a markup language and not a full-blown programming language. HTML is parsed by your web browser when a web page downloads and consists of tags (commands) which control the page layout, formatting of text, locations of images, etc.
Learn HTML
HTTP (HyperText Transfer Protocol) - HTTP is part of the TCP/IP suite of protocols and is responsible for defining the rules of exchange between a web browser and a web server . These rules dictate the exchanging of files (text, graphic images, sound, video, and other multimedia files) on the World Wide Web. . These rules dictate the exchanging of files (text, graphic images, sound, video, and other multimedia files) on the World Wide Web.
HTTPS (HyperText Transfer Protocol Secure) - HTTPS is HTTP over SSL (Secure Sockets Layer) which provides encryption for secure transactions. Developed by Netscape, this protocol is used for internet transactions where encryption of personal and financial information is paramount as in e-commerce. Secure pages will have https:// at the beginning of the URL rather than http://.
 Hub - A physical layer network device used to connect multiple Ethernet devices together. Active hubs act as a repeater and boost the signal in order to allow for it to travel farther, while passive hubs simply pass the signal through. Most hubs have an uplink port that allows them to connect to other hubs, a router, or other network device. Hub - A physical layer network device used to connect multiple Ethernet devices together. Active hubs act as a repeater and boost the signal in order to allow for it to travel farther, while passive hubs simply pass the signal through. Most hubs have an uplink port that allows them to connect to other hubs, a router, or other network device.
Hybrid Topology - Hybrid topologies are a combination of any two or more network topologies in such a way that the resulting network does not resemble any of the original topology types used to create it. Two common examples for Hybrid network are: star ring network and star bus network. A Star ring network consists of two or more star topologies connected using a multistation access unit (MAU) as a centralized hub. A Star Bus network consists of two or more star topologies connected using a bus trunk (the bus trunk serves as the network's backbone). See an example of a hybrid topology below.

ICA (Independent Computing Architecture) - ICA is a proprietary protocol for an application server system, designed by Citrix Systems. Products conforming to ICA are Citrix's WinFrame, Citrix XenApp (formerly called MetaFrame/Presentation Server), and Citrix XenDesktop products. These permit ordinary Windows applications to be run on a Windows server, and for any supported client to gain access to those applications. Besides Windows, ICA is also supported on a number of Unix server platforms and can be used to deliver access to applications running on these platforms. There is a wide range of clients supported including Windows, Mac, Unix, Linux, and various Smartphones.
ICANN (Internet Corporation for Assigned Names and Numbers) - ICANN is responsible for the global coordination of the Internet's system of unique identifiers. These include domain names (like .org, .museum and country codes like .UK), as well as the addresses used in a variety of Internet protocols. Originally, Network Solutions was responsible for assigning domain names and IP addresses, but was eventually taken over by ICANN which is a division of the U.S. Department of Commerce. ICANN Official Site
ICMP (Internet Control Message Protocol) - A part of the TCP/IP suite of protocols that handles error and control messages between hosts. It is the protocol used by the PING and TRACEROUTE commands.
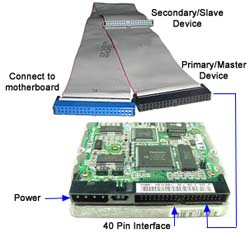 IDE (Integrated Drive Electronics) - Like SCSI, this interface is used for connecting hard drives, CD-ROMs, and other devices to the motherboard. The name of the standard was originally conceived as "PC/AT Attachment" as its primary feature was a direct connection to the 16-bit ISA bus then known as "AT bus"; the name was shortened to inconclusive "AT Attachment" or ATA to avoid possible trademark issues. IDE, a version of the ATA standard was created by Western Digital in the late '80s. Later Western Digital created EIDE (Enhanced IDE) which provided support for hard drives larger than 528mb (up to 8.4gb). The ATA standard has continued to evolve with the release of Serial ATA (SATA) in 2003. IDE (Integrated Drive Electronics) - Like SCSI, this interface is used for connecting hard drives, CD-ROMs, and other devices to the motherboard. The name of the standard was originally conceived as "PC/AT Attachment" as its primary feature was a direct connection to the 16-bit ISA bus then known as "AT bus"; the name was shortened to inconclusive "AT Attachment" or ATA to avoid possible trademark issues. IDE, a version of the ATA standard was created by Western Digital in the late '80s. Later Western Digital created EIDE (Enhanced IDE) which provided support for hard drives larger than 528mb (up to 8.4gb). The ATA standard has continued to evolve with the release of Serial ATA (SATA) in 2003.
IDS - An Intrusion Detection System is a device (or application) that monitors network and/or system activities for malicious activities or policy violations. IDS is a passive system that gives alerts when something suspicious is detected and logs the events into a database for reporting. for reporting.
IETF (Internet Engineering Task Force) - The Internet Engineering Task Force (IETF) is a large open international community of network designers, operators, vendors, and researchers concerned with the evolution of the Internet architecture and the smooth operation of the Internet. It is open to any interested individual. The IETF Mission Statement is documented in RFC 3935. The actual technical work of the IETF is done in its working groups, which are organized by topic into several areas (e.g., routing, transport, security, etc.). Much of the work is handled via mailing lists. The IETF holds meetings three times per year. IETF Official Site
IGMP – Internet Group Management Protocol is used to manage Internet Protocol multicast groups. IP hosts and adjacent multicast routers use IGMP to establish multicast group memberships. IGMP is only needed for IPv4 networks , as multicast is handled differently in IPv6 networks. , as multicast is handled differently in IPv6 networks.
IIS (Internet Information Server) - IIS is Microsoft's web server for their Windows platform that also supports writing Web-based applications that access a database. IIS also includes services for FTP, SMTP, NNTP and HTTP/HTTPS.
Image Map - An image map is a single image that is broken down into sections that can have a unique URL and other properties associated with it. For example, an image map could be an image of the United States with each state linking the user to a different web page when clicked on.
IMAP (Internet Message Access Protocol) - Like POP3, IMAP is a protocol used to access email on an email server. IMAP has some advantages over POP3 including the fact that email can be accessed and manipulated on the remote email server without having to download it.
Infrared (IrDA) - Infrared is a typically short-range line of sight networking technology which means that there cannot be obstructions between 2 devices that are trying to communicate. It is often used for file sharing between portable devices and can communicate at speeds up to 16Mbps. In certain situations, high power infrared beams transfer high-speed data from 45Mbps to 10Gbps and are installed between buildings within a few miles of each other.
Input/Output Addresses - I/O addresses are resources used by virtually every device in a computer and represent locations in memory that are designated for use by various devices to exchange information between themselves and the rest of the PC.
Intranet - An intranet is a private internal network in an enterprise. An intranet may behave similarly to the internet with web pages, FTP servers, instant messaging and other forms of communication. The difference is that these services are only made available to members of the enterprise and not the public at large.
IOS (Internetworking Operating System) - Cisco's IOS is the operating system used on Cisco Systems routers and some network switches (those which don't use CatOS). It is a multi-tasking operating system and provides kernel services such as process scheduling as well as the command line interface and routing software.
IP (Internet Protocol) - IP is a connectionless protocol, which means that a session is not created before sending data. IP is responsible for addressing and routing of packets between computers on a network. It does not guarantee delivery and does not give acknowledgement of packets that are lost or sent out of order as this is the responsibility of higher layer protocols such as TCP. IP is the backbone of the internet and most modern networks. The current IP addressing scheme is IPv4 which uses numerical addresses that appear in the form of xxx.xxx.xxx.xxx. Because we have nearly used up all of the IP addresses, a new addressing scheme called IPv6 is supposedly the next generation of IP addressing. More information...
IPS - An Intrusion Prevention System performs the role of an IDS, however, it sits inline with traffic flows on a network, actively shutting down attempted attacks as they’re sent over the wire. It can stop the attack by terminating the network connection or user session originating the attack, by blocking access to the target from the user account, IP address, or other attribute associated with that attacker, or by blocking all access to the targeted host, service, or application. Vendors are increasingly combining the two technologies into a single box, now referred to as IDPS.
IPSec (Internet Protocol Security) - A framework of open standards for ensuring secure private communications over the Internet. Based on standards developed by the Internet Engineering Task Force (IETF), IPSec ensures confidentiality, integrity, and authenticity of data communications across a public network. IPSEC is made of two different protocols: AH and ESP. AH (Authentication header) is responsible for authenticity and integrity, while ESP (Encapsulating Security payload) encrypts the payload. IPSec operates at layer 3 (network layer) of the OSI Model. Windows 2000 and newer operating systems provide support for IPSec.
IP Spoofing - A technique used to gain unauthorized access to computers, whereby the intruder gives off the appearance that the packets they are sending are coming from a trusted host. To engage in IP spoofing, an attacker must modify the packet headers so that it appears that the packets are coming from the trusted IP address.
IPv6 (Internet Protocol Version 6) - IPv6 is also known as "IP Next Generation"(IPng) and has been in development since the early '90's. The Internet Protocol has been around for almost 30 years and with the growth of the internet, this has led to a rapidly declining number of available addresses. IPv4 only supports an address space of 4,294,967,296 while IPng supports addresses which are four times the number of bits as IPv4 addresses and provides for a theoretical limit of 340,282,366,920,938,463,463,374,607,431,768,211,456 addresses! IPv6 addresses are hexidecimal and take the form of xxxx.xxxx.xxxx.xxxx.xxxx.xxxx.xxxx.xxxx.
IPX (Internetwork Packet Exchange) - IPX is a networking protocol created by Novell that is used for communication on Novell Netware based networks. IPX is a network layer datagram protocol used for connectionless communications. Higher-level protocols, such as SPX and NCP, are used for additional error recovery services. The successor to IPX is the NetWare Link Services Protocol (NLSP).
IRC (Internet Relay Chat) - Acronym for 'Internet relay chat.' An Internet-based communications system that permits people from across the world to hold real-time conversations online in a text-only format. IRC areas are divided into named 'channels,' and any user can open his or her own channel. It is mainly designed for group communication, but also allows one-to-one and private communications.
IRQ - Stands for Interrupt ReQuest. This is how a peripheral tells the CPU it needs its attention. There are specific numbers to tell the CPU which peripheral needs time and the priority. The priority is determined from least to greatest (i.e. 0 is the most important and 15 is the least). Most systems have 16 of these IRQs. Some older systems only have 9. This used to limit the numbers of things you can put in a system. Now technology has advanced so there is now IRQ sharing, but be mindful when working with ISA cards and older systems as you can run out fast.
IS-IS – Intermediate System to Intermediate System is a link state protocol that operates by forwarding network topology information throughout a network of routers. Each router then independently builds a picture of the network's topology based on the data received and the best topological path through the network to the destination. IS-IS is an Interior Gateway Protocol (IGP) typically used on larger networks.
ISA - Stands for Industry Standard Architecture and is an older PC bus architecture typically used for expansion devices such as modems and sound cards. The original form of ISA was a simple and slow 8-bit bus used on IBM PCs. Eventually, the ISA connector was stretched to allow 16-bits of data to pass through each clock cycle, bringing its speed to between 8 and 10 MHz.
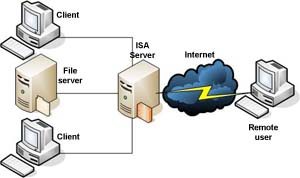 ISA Server (Internet Security & Acceleration Server) - ISA Server is an integrated edge security gateway produced by Microsoft that helps protect IT environments from Internet-based threats while providing users fast and secure remote access to applications and data. ISA Server is the successor to Microsoft's Proxy Server 2.0. ISA Server provides the two basic services of an enterprise firewall and a Web proxy/cache server. ISA Server's firewall screens all packet-level, circuit-level, and application-level traffic. The Web cache stores and serves all regularly accessed Web content in order to reduce network traffic and provide faster access to frequently-accessed Web pages. More information. ISA Server (Internet Security & Acceleration Server) - ISA Server is an integrated edge security gateway produced by Microsoft that helps protect IT environments from Internet-based threats while providing users fast and secure remote access to applications and data. ISA Server is the successor to Microsoft's Proxy Server 2.0. ISA Server provides the two basic services of an enterprise firewall and a Web proxy/cache server. ISA Server's firewall screens all packet-level, circuit-level, and application-level traffic. The Web cache stores and serves all regularly accessed Web content in order to reduce network traffic and provide faster access to frequently-accessed Web pages. More information.
ISDN (Integrated Services Digital Network) - ISDN is a type of circuit switched telephone network system designed to allow digital transmission of voice and data over ordinary telephone copper wires. The Basic Rate Interface (BRI) consists of two 64 kbps plus another lower rate channel to handle signalling. Primary Rate Interface (PRI) consists of 23 channels plus a signalling channel. Although DSL technology has caused a decline in ISDN use because of its higher bandwidth and smaller price tag, ISDN is still widely used in the United States for frame relay backup and instances where a circuit switched network is needed.
|
|
Java - Java is an object-oriented programming language developed by Sun Microsystems. The language was intended to replace C++, although the feature set better resembles that of Objective C. It can be used to build small application modules or applets for use as part of a Web page. Applets make it possible for a Web page user to interact with the page. Java should not be confused with JavaScript, which shares only the name and a similar C-like syntax. Official Site
JavaScript - JavaScript is a platform independent, client-side scripting Language which means that it is interpreted by the client's browser and not compiled on the web server. JavaScript allows webmasters to add interactive features to their sites. JavaScript was developed by Netscape and originally called LiveScript. JavaScript Tutorial
Jitter - Jitter is the deviation in or displacement of some aspect of the pulses in a high-frequency digital signal. As the name suggests, jitter can be thought of as shaky pulses. The deviation can be in terms of amplitude, phase timing, or the width of the signal pulse. Another definition is that it is "the period frequency displacement of the signal from its ideal location." Among the causes of jitter are electromagnetic interference (EMI) and crosstalk with other signals. Jitter can cause a display monitor to flicker; affect the ability of the processor in a personal computer to perform as intended; introduce clicks or other undesired effects in audio signals, and loss of transmitted data between network devices. The amount of allowable jitter depends greatly on the application.
JPEG (Joint Photographic Experts Group) - A JPEG is a 24 bit bitmap image format that can be a very efficient way to compress graphics for web sites due to its use of lossy compression. You can select how much to compress a file, and therefore how much information is lost. The JPEG format does not support animation or transparency. JPEG images use the .jpg file extension.
JScript - JScript is Microsoft's implementation of JavaScript. JScript was first supported in Internet Explorer browser 3.0 released in August, 1996.
JSP (JavaServer Pages) - JSP pages provide a simplified, fast way to create web pages that display dynamically-generated content. You can use JSP tags or scriptlets to generate the dynamic content. The logic that generates the content is encapsulated in tags and JavaBeans components and tied together in scriptlets, all of which are executed on the server side. On the server, a JSP engine interprets JSP tags and scriptlets, generates content (for example, by accessing JavaBeans components, accessing a database with JDBC technology, or including files), and sends the results back in the form of an HTML with JDBC technology, or including files), and sends the results back in the form of an HTML (or XML) page to the browser. The function of JSP is similar to ASP, however, JSP is an open standard. (or XML) page to the browser. The function of JSP is similar to ASP, however, JSP is an open standard.
 Jumpers - A metal bridge that closes an electrical circuit. Typically, a jumper consists of a plastic plug with metal contacts inside that fits over a pair of protruding pins. Jumpers are sometimes used to configure expansion boards, hard drives, and other devices. By placing a jumper plug over a different set of pins, you can change a board's parameters. Jumpers - A metal bridge that closes an electrical circuit. Typically, a jumper consists of a plastic plug with metal contacts inside that fits over a pair of protruding pins. Jumpers are sometimes used to configure expansion boards, hard drives, and other devices. By placing a jumper plug over a different set of pins, you can change a board's parameters.
Kerberos - Invented by MIT, this protocol has been evolving in the Unix world for over a decade and has become a standard in Windows operating systems. Kerberos is a network authentication protocol which utilizes symmetric cryptography to provide authentication for client-server applications. The core of a Kerberos architecture is the KDC (Key Distribution Server) that serves as the trusted third party and is responsible for storing authentication information and using it to securely authenticate users and services. In order for this security method to work, it is paramount that the KDC is available and secure. The clocks of all hosts involved must be synchronized as well. For more information read Kerberos Security. involved must be synchronized as well. For more information read Kerberos Security.
Keyboard - Keyboards are input devices for typing that connect to the motherboard. Most desktop keyboards are of the 101/102 key variety while notebook computers use smaller that usually have around 84 keys. Older AT keyboards used a 5 pin DIN connection while newer standards use a 6 pin mini DIN connector, USB, or wireless connection. use smaller that usually have around 84 keys. Older AT keyboards used a 5 pin DIN connection while newer standards use a 6 pin mini DIN connector, USB, or wireless connection.
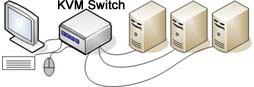 KVM Switch - A Keyboard, Video, Mouse (KVM) Switch is a device that allows multiple computers to share 1 keyboard, video monitor, and mouse. A KVM switch allows the user to interact only with one computer at a time, but a series of key strokes or other method can be used to switch computers. KVM Switch - A Keyboard, Video, Mouse (KVM) Switch is a device that allows multiple computers to share 1 keyboard, video monitor, and mouse. A KVM switch allows the user to interact only with one computer at a time, but a series of key strokes or other method can be used to switch computers.
|
L2TP (Layer 2 Tunneling Protocol) - Published in 1999 as proposed standard RFC 2661, L2TP has its origins primarily in two older tunneling protocols for PPP: Cisco's Layer 2 Forwarding (L2F) and Microsoft's Point-to-Point Tunneling Protocol (PPTP). A new version of this protocol, L2TPv3, was published as proposed standard RFC 3931 in 2005. L2TPv3 provides additional security features, improved encapsulation, and the ability to carry data links other than simply PPP over an IP network (e.g., Frame Relay, Ethernet, ATM, etc). L2TP acts as a data link layer (layer 2 of the OSI model) protocol for tunneling network traffic between two peers over an existing network (usually the Internet). It is common to carry Point-to-Point Protocol (PPP) sessions within an L2TP tunnel. L2TP does not provide confidentiality or strong authentication by itself. IPsec is often used to secure L2TP packets by providing confidentiality, authentication and integrity. The combination of these two protocols is generally known as L2TP/IPsec.
 LAN (Local Area Network) - A computer network that spans a relatively small area and typically offers high-speed communications. Most LANs are confined to a single building or group of buildings. However, one LAN can be connected to other LANs over any distance via telephone LAN (Local Area Network) - A computer network that spans a relatively small area and typically offers high-speed communications. Most LANs are confined to a single building or group of buildings. However, one LAN can be connected to other LANs over any distance via telephone lines, coaxial cable, wi-fi, etc. A system of LANs connected in this way is called a wide area network (WAN). Most LANS of today utilize Ethernet and/or Wi-Fi connections. lines, coaxial cable, wi-fi, etc. A system of LANs connected in this way is called a wide area network (WAN). Most LANS of today utilize Ethernet and/or Wi-Fi connections.
Latency - (AKA "lag") is the amount of time it takes a packet of data to move across a network connection. When a packet is being sent, there is "latent" time, when the computer that sent the packet waits for confirmation that the packet has been received. Latency and bandwidth are the two factors that determine your network connection speed. Latency in a packet-switched network is measured either one-way (the time from the source sending a packet to the destination receiving it), or round-trip (the one-way latency from source to destination plus the one-way latency from the destination back to the source). Round-trip latency is more often quoted, because it can be measured from a single point. Note that round trip latency excludes the amount of time that a destination system spends processing the packet. Many software platforms provide a service called ping that can be used to measure round-trip latency. Ping performs no packet processing; it merely sends a response back when it receives a packet, thus it is a relatively accurate way of measuring latency.
LDAP (Lightweight Directory Access Protocol) - A protocol used to access listings in hierarchical information directories (databases). LDAP is a simplified version of the standard used to gain access to X.500 directories. Microsoft's Active Directory which was first released in Windows 2000 utilizes LDAP for locating records in the directory.
Link State Routing Protocols – are one of the two main classes of routing protocols used in packet switching networks and includes protocols such as Open Shortest Path First (OSPF) and Intermediate System to Intermediate System (IS-IS). The link-state protocol is performed on every router on the network, where every routing node constructs a map of the connectivity to the network by showing which nodes are connected to each other. Each router calculates the next best logical hop from it to every possible known destination which forms the node's routing table. and includes protocols such as Open Shortest Path First (OSPF) and Intermediate System to Intermediate System (IS-IS). The link-state protocol is performed on every router on the network, where every routing node constructs a map of the connectivity to the network by showing which nodes are connected to each other. Each router calculates the next best logical hop from it to every possible known destination which forms the node's routing table.
Lithium-Ion - Lithium-ion rechargeable batteries generally provide more energy capacity than nickel based types of the same weight. They also do not suffer from "memory effect" and are non-toxic. These batteries are used in many devices including laptops, cell phones, and digital cameras.
Load Balancing - is a technique to distribute workload evenly across two or more computers, network links, CPUs, hard drives, or other resources, in order to get optimal resource utilization, maximize throughput, minimize response time, and avoid overload. Using multiple components with load balancing, instead of a single component, may increase reliability through redundancy. The load balancing service is usually provided by a dedicated program or hardware device (such as a multilayer switch or a DNS server).
|
NAT (Network Address Translation) - NAT is a service in which the source and/or destination addresses of IP packets are rewritten as they pass through a router or firewall. It is most commonly used to enable multiple hosts on a private network to access the Internet using a single public IP address. NAT is typically used for security reasons. on a private network to access the Internet using a single public IP address. NAT is typically used for security reasons.
NBTSTAT - Is used to troubleshoot connectivity problems between 2 computers communicating via NetBT, by displaying protocol statistics and current connections. NBTSTAT examines the contents of the NetBIOS name cache and gives MAC address.
NDA (Non-disclosure Agreement) - Before taking most certification exams, you will need to accept the terms of the NDA. While they vary from one certification vendor to another, the general message of these agreements is that you will not share information about the exam you have taken with others after you have taken it.
Microsoft's NDA
CompTIA Candidate Agreement
Cisco's Certification Exam Policies
NDIS (Network Device Interface Specification) - NDIS is a Windows device driver API that enables a single network interface card (NIC) to support multiple network protocols. For example, with NDIS a single NIC can support both TCP/IP and IPX connections. The NDIS is a Logical Link Control (LLC) that forms the upper sublayer of the OSI data link layer (layer 2 of 7) and acts as an interface between layer 2 and 3 (the Network Layer). The lower sublayer is the Media Access Control (MAC) device driver. NDIS was jointly developed by Microsoft and 3Com Corporation, and is nowadays mostly used in Windows, but the open-source ndiswrapper and Project Evil driver wrapper projects allow many NDIS-compliant NICs to be used with Linux and FreeBSD, respectively. magnussoft ZETA, a derivative of BeOS, supports a number of NDIS drivers.
NetBEUI - Stands for "NetBIOS Extended User Interface". It is a transport layer protocol mainly used for small Windows 9x and NT LANs. In reference to the NetBIOS distinction, NetBIOS is the applications programming interface and NetBEUI is the transport protocol. NetBEUI is a non-routable protocol meaning it will not allow communication through a router. It is broadcast oriented which causes it to not scale well. Although it can still be installed on newer Microsoft operating systems, it has largely been replaced by TCP/IP.
 NIC (Network Interface Card) - A Network Interface Card is an expansion board you insert into a computer so the computer can be connected to a network. Most NICs are designed for a particular type of network, protocol and media, although some can serve multiple networks NIC (Network Interface Card) - A Network Interface Card is an expansion board you insert into a computer so the computer can be connected to a network. Most NICs are designed for a particular type of network, protocol and media, although some can serve multiple networks . .
NiCd (Nickel-Cadmium) - Nickel-cadmium batteries (commonly abbreviated NiCd or NiCad) are a popular type of rechargeable battery for portable electronics, cordless phones, power tools, and other devices. NiCd batteries are known for the "memory effect" that they develop if repeatedly charged without being fully discharged. They are also not environmentally friendly.
NiMH (Nickel Metal Hydride) - A type of rechargeable battery similar to a nickel-cadmium (NiCd) battery but has a hydride absorbing alloy for the anode instead of cadmium, which is an environmental hazard. A NiMH battery can have two to three times the capacity of an equivalent size NiCd and the memory effect is not as significant. However, compared to the lithium ion chemistry, the volumetric energy density is lower and self-discharge is higher. Applications of NiMH type batteries includes hybrid vehicles such as the Toyota Prius and consumer electronics. Standard NiMH batteries perform better with moderate drain devices such as digital cameras, flashlights, and other consumer electronics, but, because NiCd batteries have lower internal resistance, they still have the edge in very high current drain applications such as cordless power tools and RC cars.
NNTP (Network News Transfer Protocol) - This protocol's primary purpose is to provide a mechanism for Usenet news servers (NNTP Servers) to communicate with each other and with newsreader clients. This allows for the creation of newsgroups. A newsgroup is a discussion about a particular subject consisting of notes written to a central Internet site and redistributed through Usenet, a worldwide network of news discussion groups.
 NSLOOKUP - This is a command that queries a DNS server for machine name and address information. Originally written for Unix operating systems, this command is now available on Windows and other operating systems. To use nslookup, type "nslookup" followed by an IP address, a computer name, or a domain name. NSLOOKUP will return the name, all known IP addresses and all known aliases (which are just alternate names) for the identified machine. NSLOOKUP is a useful tool for troubleshooting DNS problems. NSLOOKUP - This is a command that queries a DNS server for machine name and address information. Originally written for Unix operating systems, this command is now available on Windows and other operating systems. To use nslookup, type "nslookup" followed by an IP address, a computer name, or a domain name. NSLOOKUP will return the name, all known IP addresses and all known aliases (which are just alternate names) for the identified machine. NSLOOKUP is a useful tool for troubleshooting DNS problems.
NTFS (New Technology File System) - NTFS is the standard file system of Windows NT and its descendants Windows 2000, Windows XP and Windows Server 2003. Windows version 95, 98, 98SE and ME, cannot natively read NTFS filesystems, although utilities do exist for this purpose. NTFS offers additional features over FAT and FAT32 predecessors such as transaction logs to help recover from disk failures, the ability to set permissions for directories and/or individual files, support for large hard drives, support for long filenames, etc.
|
OFDM (Orthogonal Frequency-Division Multiplexing) - OFDM is a digital multi-carrier modulation scheme, which uses a large number of closely-spaced orthogonal sub-carriers. Each sub-carrier is modulated with a conventional modulation scheme (such as quadrature amplitude modulation) at a low symbol rate, maintaining data rates similar to conventional single-carrier modulation schemes in the same bandwidth. In practice, OFDM signals are generated using the Fast Fourier transform algorithm. The primary advantage of OFDM over single-carrier schemes is its ability to cope with severe channel conditions — for example, attenuation of high frequencies at a long copper wire, narrowband interference and frequency-selective fading due to multipath — without complex equalization filters. Channel equalization is simplified because OFDM may be viewed as using many slowly-modulated narrowband signals rather than one rapidly-modulated wideband signal. Low symbol rate makes the use of a guard interval between symbols affordable, making it possible to handle time-spreading and eliminate inter-symbol interference (ISI). OFDM is used in many applications including DSL and 802.11 a/g wireless networking. networking.
Open Relay - Also referred to as an open relay server, an SMTP e-mail server that allows a third party to relay e-mail messages, ie, sending and/or receiving e-mail that is not for or from a local user. Spammers essentially hijack open relays and use them to send out massive quantities of unsolicited email (UCE).
OSI Model (Open Systems Interconnection Model) - Developed by the International Standards Organization (ISO), the OSI reference model is a 7 layer networking framework that divides the networking process into logical layers. The 7 layers are: Physical, Data Link (which has sub-layers called Media Access Control and Logical Link Control), Network, Transport, Session, Presentation, and Application. OSI Model
OSPF (Open Shortest Path First) - This is a link-state routing protocol that converges faster than a distance vector protocol such as RIP. What is convergence? This is the time required for all routers to complete building of the routing tables. RIP uses ticks and hop counts as measurement, while OSPF also uses metrics that takes bandwidth and network congestion into making routing decisions. RIP transmits updates every 30 seconds, while OSPF transmits updates only when there is a topology change. OSPF builds a complete topology of the whole network, while RIP uses second handed information from the neighboring routers. To summarize, RIP is easier to configure, and is suitable for smaller networks . In contrast, OSPF requires high processing power, and is suitable if scalability is the main concern. . In contrast, OSPF requires high processing power, and is suitable if scalability is the main concern.
OSPF E2 Routes vs. E1 Routes
OSPF Autonomous Border System Routers Explained And Illustrated
Route Summarization And The OSPF Null Interface
Overclocking - This term refers to configuring a computer component run at a higher clock speed than the manufacturer's specifications. The main reason this is done is to increase hardware performance. Overclocking does not come without risks as it can result in system instablity or even cause hardware failure in some situations.
|
Packet Loss - is the failure of one or more transmitted packets to arrive at their destination. This event can cause noticeable effects in all types of digital communications. The causes of packet loss include inadequate signal strength at the destination, natural or human-made interference, excessive system noise, hardware failure, software corruption or overburdened network nodes. Often more than one of these factors is involved. In a case where the cause cannot be remedied, concealment may be used to minimize the effects of lost packets.
Packet Shaping - See "Traffic Shaping".
Packet Sniffer - A packet sniffer is a device or software used to capture packets traveling over a network connection. The packets are logged and can be decoded in order to provide information and statistics about the traffic on the network or network segment. These tools are used for troubleshooting difficult network problems, monitoring network traffic, and detecting intrusion attempts. Also known as Packet Analyzers.
Packet Switching - Packets transmitted from "point A" to "point B" all have to arrive at the same destination, but with packet switching, they do not all have to take the same path to get there. Packets can take different paths to get from source to destination, but the end result is that all the packets arrive at the destination. The packets are then reassembled to take the form of the original message. Packet switching is a very efficient way of transporting data, however, if there are packets that must arrive at the destination in the same order in which they left the source, packet switching isn't a good choice. Frame Relay is a packet switching technology, as is X.25, and both of these protocols are highly efficient.
Introduction to WAN Technologies
 Parallel Port - A parallel port is used to connect printers to computers. This connector stands out as the biggest connector (usually) on the back of your PC. It is usually next to the serial ports. It is a DB-25 connector on the PC and usually a Centronics 36 pin connection to the peripheral. *Warning* There are SCSI 1 connectors that look like this and will actually fit together - Doing so can potentially damage your printer or PC. Just look for the SCSI symbol to tell the difference. Parallel Port - A parallel port is used to connect printers to computers. This connector stands out as the biggest connector (usually) on the back of your PC. It is usually next to the serial ports. It is a DB-25 connector on the PC and usually a Centronics 36 pin connection to the peripheral. *Warning* There are SCSI 1 connectors that look like this and will actually fit together - Doing so can potentially damage your printer or PC. Just look for the SCSI symbol to tell the difference.
PAT – Port Address Translation is a feature of a network device that translates TCP or UDP communications made between hosts on a private network and hosts on a public network. It allows a single public IP address to be used by many hosts on a private network.
 Patch Panel - A panel of network ports contained together, usually within a wiring closet, that connects incoming and outgoing lines of a LAN or other communication, electronic or electrical systems. In a LAN, the patch panel connects the network's computers to each other and to the outside lines that enable the LAN to connect to the Internet or another WAN. Connections are made with patch cables. Patch Panel - A panel of network ports contained together, usually within a wiring closet, that connects incoming and outgoing lines of a LAN or other communication, electronic or electrical systems. In a LAN, the patch panel connects the network's computers to each other and to the outside lines that enable the LAN to connect to the Internet or another WAN. Connections are made with patch cables.
PATHPING - PATHPING is a network utility supplied in later versions of Windows (NT, 2000, 2003, XP). It combines the functionality of Ping with that of the traceroute command (in Windows: tracert), by providing details of the path between two hosts and ping-like statistics for each node in the path based on samples taken over a time period, depending on how many nodes are between the start and end host. The command is entered as pathping ip_address/hostname.
 PCI - Stands for Peripheral Component Interconnect and is personal computer local bus designed by Intel. It provides a high-speed connection at 33Mhz with peripherals and allows connection of seven peripheral devices. It is mostly used with Pentium computers but is processor independent and therefore able to work with other processors. Supports PnP, Burst Mode, Bus Mastering. Utilizes the host bridge to communicate with other types of expansion slots. The 32-bit version is the most common and it has displaced ISA and VESA architectures. PCI - Stands for Peripheral Component Interconnect and is personal computer local bus designed by Intel. It provides a high-speed connection at 33Mhz with peripherals and allows connection of seven peripheral devices. It is mostly used with Pentium computers but is processor independent and therefore able to work with other processors. Supports PnP, Burst Mode, Bus Mastering. Utilizes the host bridge to communicate with other types of expansion slots. The 32-bit version is the most common and it has displaced ISA and VESA architectures.
PCI Express - A newer bus that is also known as PCIe. PCI Express is an implementation of the PCI computer bus that uses existing PCI programming concepts, but bases it on a completely different and much faster serial physical-layer communications protocol. It provides much faster speeds and is backward compatible with traditional PCI. The 64-bit version is more common than the 32-bit.
PDC Emulator (Primary Domain Controller Emulator) - With regards to Active Directory, the PDC Emulator acts like a PDC from a Windows NT 4.0 network and is necessary in domains that are not pure Windows 2000 or 2003 (i.e have Windows 95/98/NT down-level clients). If the domain is running in Native Mode then this server is the "preferred" replication partner for the other DCs for password changes and also handles account lockouts and authentication failures.
PDF (Portable Document Format) - Created by Adobe, PDF files can be read on any platform with Adobe’s Acrobat Reader. In order to view PDF files in a web browser, a plug-in must be installed.
PDL (Page Description Language) - PDLs are programming languages used to "describe" the contents of a page in terms that a printer can understand. When sent to the printer, a document is parsed by the driver which converts the document into the language that the printer understands and instructs the printer how to format the document. Adobe's PostScript and HP's Printer Control Language (PCL) are the 2 most common PDLs used in desktop publishing.
Peripherals - Peripherals are composed of input and output devices including the mouse, keyboard, monitor, speakers, printer, etc. Mice and keyboards are input devices since they are used to provide the computer with information. Output devices provide YOU with information such as speakers, printers and the monitor.
Perl (Practical Extraction and Reporting Language) - Perl is a server-side script programming language that is used largely as a language for developing CGI programs. CGI stands for Common Gateway Interface and is a standard way for a Web server to pass a Web user's request to an application program. CGI programs can tend to be server intensive. Perl requires that a Perl Interpreter is loaded on the web server. To some degree, Perl has been replaced by programming languages like ASP and PHP.
Permissions - The way permissions work varies among operating systems. In general, A permission is authorization to perform an operation on a specific object, such as a file or a share. Permissions are granted by owners. If you own an object, you can grant any user or security group permission to do whatever you are authorized to do with it.
Windows 2000/2003 NTFS and Share Permissions
Phishing - Phishing, a form of social engineering, is the fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication such as email, chat, or instant messaging.
PHP - PHP is a powerful, general-purpose, server-side scripting language that is especially suited for web development and can be embedded into HTML. PHP lets you create dynamic web pages which are treated just like regular HTML pages and you can create and edit them the same way you normally create regular HTML pages. PHP is designed for use on Linux/Unix web servers and PHP applications are frequently used in conjunction with a MySQL database . .
PING (Packet InterNet Groper) - PING is a command-line utility used to verify connections between networked devices. PING uses ICMP echo requests that behave similarly to SONAR pings. The standard format for the command is ping ip_address/hostname. If successful, the ping command will return replies from the remote host with the time it took to receive the reply. If unsuccessful, you will likely recieve and error message.
Ping Flooding - The ping utility utilizes the ICMP protocol. A Ping Flooding attack is one in which the server is overloaded with Ping requests that it cannot keep up with. A similar attack called "Ping of Death" sends overly large packets (over 64 bytes) to computer which will shut it down if it is not able to handle packets of that size.
PKI (Public Key Infrastructure) - A public key infrastructure (PKI) is the combination of software, encryption technologies, processes, and services that enable an organization to secure its communications and business transactions. PKI uses a public and a private cryptographic key pair that is obtained and shared through a trusted authority. The public key infrastructure provides for a digital certificate that can identify an individual or an organization and directory services that can store and, when necessary, revoke the certificates.
PNG (Portable Network Graphics) - The PNG image file format was designed to replace the GIF format, and challenge JPEG for many purposes. PNG is capable of color depths from two colors, or 1 bit, to 16.7 million colors with an Alpha channel, or 32 bit and supports transparency.
PoE - Generally speaking, Power over Ethernet technology describes a system to safely pass electrical power, along with data, on Ethernet cabling. Standard versions of PoE specify category 5 cable or higher. Power can come from a power supply within a PoE-enabled networking device such as an Ethernet switch or from a device built for "injecting" power onto the Ethernet cabling. IP Phones, LAN access points, and WiFi switches to RFID readers and network security cameras. All of these require more power than USB offers and very often must be powered over longer runs of cable than USB permits. In addition, PoE uses only one type of connector, an 8P8C (RJ45), whereas there are four different types of USB connectors.
 POP3 (Post Office Protocol) - POP3 is the protocol used to retrieve messages from a mail server. POP3 facilitates the downloading of messages to an email client such as Microsoft Outlook or Eudora. IMAP is an alternative to POP3 that offers more features, but currently POP3 is the most commonly used protocol for this purpose. POP3 utilizes port 110. POP3 (Post Office Protocol) - POP3 is the protocol used to retrieve messages from a mail server. POP3 facilitates the downloading of messages to an email client such as Microsoft Outlook or Eudora. IMAP is an alternative to POP3 that offers more features, but currently POP3 is the most commonly used protocol for this purpose. POP3 utilizes port 110.
RFC 1939
POP3 Protocol
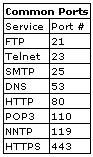 Port1 - A single PC may be sending email, receiving a Telnet request, and accessing the Internet at the same time. Ports keep these "conversations" separate. Each potential type of conversation a host can have is preassigned a port number, and these port numbers allow different types of communications to take place over the same physical cable by keeping them logically separated. Port1 - A single PC may be sending email, receiving a Telnet request, and accessing the Internet at the same time. Ports keep these "conversations" separate. Each potential type of conversation a host can have is preassigned a port number, and these port numbers allow different types of communications to take place over the same physical cable by keeping them logically separated.
Ports, Port Numbers, and Sockets
Port2 - To move software from one computer to another. To rewrite software to make it able to run in another environment or on a different operating system.
Port Authentication - The IEEE 802.1x standard defines 802.1x port-based authentication as a client-server based access control and authentication protocol that restricts unauthorized clients from connecting to a LAN through publicly accessible ports. The authentication server validates each client connected to a switch port before making available any services offered by the switch or the LAN.
Port Mirroring - Used on a network switch to send a copy of network packets seen on one switch port (or an entire VLAN) to a network monitoring connection on another switch port. This is commonly used for network appliances that require monitoring of network traffic, such as an intrusion-detection system.
Port Scanner - A port scanner is a program designed to probe network hosts for open ports. This is often used by administrators to verify security policies of their networks and by attackers to identify running services on a host that can be exploited to gain access. and by attackers to identify running services on a host that can be exploited to gain access.
PostScript - PostScript is a page description language (PDL) developed by Adobe Systems in 1982. Since that time, it has gone through a couple of revisions and the current level is PostScript 3. PostScript, often referred to as PS, is the dominant programming language used in the desktop publishing industry. When a document is sent to a PostScript printer, the document is parsed by the driver which converts the document into PostScript code. This code is sent to the printer which has a PostScript interpreter. The code tells the interpreter how to format the page, which colors to use, which fonts, and everything else needed to output the document correctly.
Official PostScript Site
 Power Supply - The power supply converts electricity received from a wall outlet (120V AC in the USA) into DC current amounts that are needed by the various components of a computer system. Power Supply - The power supply converts electricity received from a wall outlet (120V AC in the USA) into DC current amounts that are needed by the various components of a computer system.
PPP (Point to Point Protocol) - Provides a standard means of encapsulating data packets sent over a single-channel WAN link. Specifically, PPP provides a method for connecting a personal computer to the Internet using a standard phone line and a modem using a serial connection. PPP replaced SLIP as the standard for dial-up connections as it supports more protocols than just TCP/IP.
Configuring PPP Callback
PPPoE (Point to Point Protocol over Ethernet) - In the past, most internet users were connected to the internet via a serial modem, however, current technologies have replaced dial-up internet connections with DSL and cable, for example. In short, PPPoE is a network protocol for encapsulating PPP frames in Ethernet frames.
PPTP (Point to Point Tunneling Protocol) - The Point to Point Tunneling Protocol (PPTP) provides for the secure transfer of data from a remote client to a private server by creating a multi-protocol Virtual Private Network(VPN) which encapsulates PPP packets into IP datagrams. It is mostly used to allow corporations to extend their own corporate network through private "tunnels" over the public Internet.
Processor - (See CPU)
Proxy Server - A proxy server acts as a middle-man between clients and the Internet providing security, administrative control, and caching services. When a user makes a request for an internet service and it passes filtering requirements, the proxy server looks in its local cache of previously downloaded web pages. If the item is found in cache, the proxy server forwards it to the client. This reduces bandwidth through the gateway. If the page is not in the cache, the proxy server uses one of its own IP addresses to request the page from the appropriate server.
|
QoS (Quality of Service) - A communications networks transport a multitude of applications and data, including high-quality video and delay-sensitive data such as real-time voice. The bandwidth-intensive applications stretch network capabilities and resources, but also complement, add value, and enhance every business process. Networks must provide secure, predictable, measurable, and sometimes guaranteed services. Achieving the required Quality of Service (QoS) by managing the delay, delay variation (jitter), bandwidth, and packet loss parameters on a network becomes the secret to a successful end-to-end business solution. Thus, QoS is the set of techniques to manage network resources transport a multitude of applications and data, including high-quality video and delay-sensitive data such as real-time voice. The bandwidth-intensive applications stretch network capabilities and resources, but also complement, add value, and enhance every business process. Networks must provide secure, predictable, measurable, and sometimes guaranteed services. Achieving the required Quality of Service (QoS) by managing the delay, delay variation (jitter), bandwidth, and packet loss parameters on a network becomes the secret to a successful end-to-end business solution. Thus, QoS is the set of techniques to manage network resources . .
Queue - In printing, documents sent to a printer are ripped by the driver and then placed in a holding space called the print queue. Documents are pulled out of the queue as the printer becomes available. By default this occurs on a "first in, first out" (FIFO) basis, although most operating systems offer the ability to control the priority of the print jobs. The service that the print queue provides is also referred to as print spooling.
 QWERTY - Pronounced "kwerty", QWERTY refers to the first 6 letters in the upper left corner of an English-language keyboard. This keyboard layout was developed by Christopher Sholes in 1868. The keys were layed out in this manner to increase productivity. QWERTY - Pronounced "kwerty", QWERTY refers to the first 6 letters in the upper left corner of an English-language keyboard. This keyboard layout was developed by Christopher Sholes in 1868. The keys were layed out in this manner to increase productivity.
|
RADIUS - Remote Authentication Dial In User Service (RADIUS) is a networking protocol that provides centralized Authentication, Authorization, and Accounting (AAA) management for computers to connect and use a network service. RADIUS is often used by ISPs and enterprises to manage access to the Internet or internal networks , and wireless networks. Microsoft's answer to corporate wireless security is the use of RADIUS authentication through its Internet Authentication Services (IAS) product. , and wireless networks. Microsoft's answer to corporate wireless security is the use of RADIUS authentication through its Internet Authentication Services (IAS) product.
RAID (Redundant Array of Inexpensive Disks) - RAID employs two or more drives in combination for fault tolerance and/or performance. There are different raid configurations that are referred to as "levels". Raid levels 0 (Disk Stiping Without Parity), 1 (Disk Mirroring), and 5 (Disk Stiping With Parity) are the most common varieties. See the links below for in-depth descriptions of the various raid levels.
Terms and Concepts of Hardware and Software RAID - PART 1
Terms and Concepts of Hardware and Software RAID - PART 2
RAM - Stands for Random Access Memory. RAM volatile memory and its contents can be accessed in any order unlike other storage methods (hard drive, floppy, CDROM, etc). Computers use RAM to hold the program code and data during execution. Over the years a variety of memory types have emerged including DIP, SIP, SIMM, DIMM, RIMM, etc.
RAS (Remote Access Service) - RAS refers to any combination of hardware and software to enable remote access to a network. A RAS server is a specialized computer which aggregates multiple communication channels together. An example of this would be a server that dial-up users dial into. The term was originally coined by Microsoft during the Windows NT era and is now called Routing and Remote Access Service (RRAS).
RDP (Remote Desktop Protocol) - Originally released with Windows NT 4.0 Terminal Services, RDP 4.0 allowed users to connect to a computer and remotely control (AKA Shadow) it. With the release of Windows Vista and upcoming Windows Longhorn, version 6.0 will allow one to connect to specific applications rather than the entire desktop of the remote computer. Remote Desktop allows systems administrators to remotely connect to a user's computer for technical support purposes, or connect to a server for maintenance and administration purposes. By default, RDP uses TCP port 3389. Understanding the Remote Desktop Protocol (RDP)
 RDRAM - Rambus DRAM adds support for even faster bus speeds and first surfaced around the time of the Pentium IV. RDRAM uses RIMMS which require a heat spreader to be attached to the RIMM to deal with its increased heat levels. Unused slots on a RDRAM motherboard must be terminated with a CRIMM in order to function. Although it is faster than many other types of RAM, the technology never really caught on due to high prices. RDRAM - Rambus DRAM adds support for even faster bus speeds and first surfaced around the time of the Pentium IV. RDRAM uses RIMMS which require a heat spreader to be attached to the RIMM to deal with its increased heat levels. Unused slots on a RDRAM motherboard must be terminated with a CRIMM in order to function. Although it is faster than many other types of RAM, the technology never really caught on due to high prices.
Registry - A central hierarchical database used in Microsoft Windows 9x, CE, NT, 2000, 2003, and XP. The registry is used to store information necessary to configure the system for one or more users, applications and hardware devices. The Registry contains information that Windows continually references during operation, such as profiles for each user, the applications installed on the computer and the types of documents that each can create, property sheet settings for folders and application icons, what hardware exists on the system, and the ports that are being used. A registry hive is a group of keys, subkeys, and values in the registry that has a set of supporting files containing backups of its data. The supporting files for all hives except HKEY_CURRENT_USER are in the Systemroot\System32\Config folder on Windows NT 4.0, Windows 2000, Windows XP, and Windows Server 2003; the supporting files for HKEY_CURRENT_USER are in the Systemroot\Profiles\Username folder. The file name extensions of the files in these folders, and, sometimes, a lack of an extension, indicate the type of data they contain. used in Microsoft Windows 9x, CE, NT, 2000, 2003, and XP. The registry is used to store information necessary to configure the system for one or more users, applications and hardware devices. The Registry contains information that Windows continually references during operation, such as profiles for each user, the applications installed on the computer and the types of documents that each can create, property sheet settings for folders and application icons, what hardware exists on the system, and the ports that are being used. A registry hive is a group of keys, subkeys, and values in the registry that has a set of supporting files containing backups of its data. The supporting files for all hives except HKEY_CURRENT_USER are in the Systemroot\System32\Config folder on Windows NT 4.0, Windows 2000, Windows XP, and Windows Server 2003; the supporting files for HKEY_CURRENT_USER are in the Systemroot\Profiles\Username folder. The file name extensions of the files in these folders, and, sometimes, a lack of an extension, indicate the type of data they contain.
| Key | Definition |
| HKEY_CURRENT_USER | Contains the root of the configuration information for the user who is currently logged on and contains their profile. |
| HKEY_USERS | Contains the root of all user profiles on the computer. HKEY_CURRENT_USER is an alias for a subkey in the HKEY_USERS subtree. |
| HKEY_LOCAL_MACHINE | Contains configuration information particular to the computer(for any user). |
| HKEY_CLASSES_ROOT | A subkey of HKEY_LOCAL_MACHINE\Software. The information stored here ensures that the correct program opens when you open a file by using Windows Explorer. |
| HKEY_CURRENT_CONFIG | Contains information about the hardware profile used by the local computer at system startup. |
| Registry Hive | Supporting Files |
| HKEY_LOCAL_MACHINE\SAM | Sam, Sam.log, Sam.sav |
| HKEY_LOCAL_MACHINE\Security | Security, Security.log, Security.sav |
| HKEY_LOCAL_MACHINE\Software | Software, Software.log, Software.sav |
| HKEY_LOCAL_MACHINE\System | System, System.alt, System.log, System.sav |
| HKEY_CURRENT_CONFIG | System, System.alt, System.log, System.sav, Ntuser.dat, Ntuser.dat.log |
| HKEY_USERS\DEFAULT | Default, Default.log, Default.sav |
Back up the registry
Differences between Regedit.exe and Regedt32.exe
Repeater - A physical layer device that boosts signals in order to allow a signal to travel farther and prevent attenuation. Attentuation is the degradation of a signal as it travels farther from its origination. Repeaters do not filter packets and will forward broadcasts. Both segments must use the same access method, which means that you can't connect a token ring segment to an Ethernet segment. Repeaters can connect different cable types.
RFC (Request for Comments) - The standards upon which the Internet is based, including all of its common protocols, are described in numbered documents known as RFCs. They are published and coordinated by the Internet Engineering Task Force (IETF).
IETF RFC Page
RID Master (Relative Identifier Master) - With regards to Active Directory, the RID Master works with domain controllers to assign unique SIDS to each object that requires one. Each object gets a domain SID that is common to all objects in a domain. What makes SIDS unique is the RID which is unique to all objects in the domain. The RID Master is also responsible for removing an object from its domain and putting it in another domain when an object is moved.
Rights - A user right is authorization to perform an operation that affects an entire computer rather than a specific object on the computer. User rights are divided into two categories: logon rights and privileges . Logon rights control how human users and other security principals are authorized to access a computer—at the keyboard, through a network connection, as a service, or as a batch job. Privileges control which users are authorized to manipulate system resources—by setting the computer's internal clock, for example, by loading and unloading device drivers, by backing up or restoring files and folders, or by doing anything else that affects the system as a whole.
RIMM - A RIMM is a form of memory connection much like a SIMM or DIMM. RIMM stands for Rambus Inline Memory Module and is used for RDRAM memory.
Ring Topology - A ring network is a Local Area Network where each network computer and device are connect to each other forming a large large circle (or similar shape). Each packet is sent around the ring until it reaches its final destination. A break in the circle can cause performance and connection problems. Ring networks aren't very common anymore. Token Ring/IEEE 802.5 and FDDI networks use ring topologies.
RIP (Routing Information Protocol) - RIP is a distance vector dynamic routing protocol. RIP measures the distance from source to destination by counting the number of hops(routers or gateways) that the packets must travel over. RIP sets a maximum of 15 hops and considers any larger number of hops unreachable. RIP's real advantage is that if there are multiple possible paths to a particular destination and the appropriate entries exist in the routing table, it will choose the shortest route. RIP is best used on smaller networks as larger ones can have so many entries in the routing table that the network performance can suffer.
Configuring RIP (Cisco)
 RJ-11 - Short for Registered Jack-11, a four or six-wire connector used primarily to connect telephone equipment in the United States. The cable itself is called category 1 (Cat 1). RJ-11 - Short for Registered Jack-11, a four or six-wire connector used primarily to connect telephone equipment in the United States. The cable itself is called category 1 (Cat 1).
 RJ-45 - Short for Registered Jack-45, it is an eight-wire connector used commonly to connect devices on Ethernet LANs. RJ-45 connectors look similar to RJ-11 connectors used for connecting telephone equipment, but they are larger. RJ-45 - Short for Registered Jack-45, it is an eight-wire connector used commonly to connect devices on Ethernet LANs. RJ-45 connectors look similar to RJ-11 connectors used for connecting telephone equipment, but they are larger.
Rogue Access Point - This term most often refers to unauthorized access points that are deployed with malicious intent. But in general, it would refer to any unauthorized device regardless of its intent. Types of Rogue APs could include one installed by an employee without proper consent, a misconfigured AP that presents a security risk, AP from neighboring WLANs, or one used by an attacker. To prevent the installation of rogue access points, organizations can install wireless intrusion prevention systems to monitor the radio spectrum for unauthorized access points.
ROM - ROM stands for Read Only Memory and is non-volatile. This means that the information is stored even when the power is turned off to the computer. An example of this would be the computer's BIOS settings that are retained even when the computer is off. Recent advancements in EEPROM technologies have produced Flash ROM chips that can be updated from a disk or over the internet.
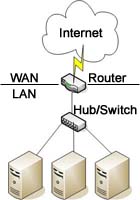 Router - Functioning at the network later of the OSI model, a router is similar to a switch, but it can also connect different logical networks or subnets and enable traffic that is destined for the networks on the other side of the router to pass through. Routers create or maintain a table of the available routes and can be configured to use various routing protocols to determine the best route for a given data packet. Routers can connect networks that use disimilar protocols. Routers also typically provide improved security functions over a switch. Router - Functioning at the network later of the OSI model, a router is similar to a switch, but it can also connect different logical networks or subnets and enable traffic that is destined for the networks on the other side of the router to pass through. Routers create or maintain a table of the available routes and can be configured to use various routing protocols to determine the best route for a given data packet. Routers can connect networks that use disimilar protocols. Routers also typically provide improved security functions over a switch.
RS-232 - A standard for serial binary data interconnection between a DTE (Data terminal equipment) and a DCE (Data communication equipment). It is commonly used in computer serial ports. RS-232 Data Interface
RTP – Real-time Transport Protocol works at the Application Layer of the Internet Protocol Suite and is the audio and video protocol standard used to deliver content over the Internet. RTP is used in conjunction with other protocols such as H.323 and RTSP.
SATA (Serial Advanced Technology Attachment) - SATA is an evolution of the Parallel ATA physical storage interface. Serial ATA is a serial link - a single cable with a minimum of four wires creates a point-to-point connection between devices. Transfer rates for Serial ATA begin at 150 MBps and SATA II 300MBps. This newer specification that offers a number of benefits including: Faster throughput, thinner 7-pin cable (as opposed to the IDE 40 pin ribbon cable) that promotes better airflow through the case, support for longer cables, and hot-swappable. In addition, there are no jumpers to worry about because each device connects to its own controller channel.
Schema - When referring to Active Directory, a schema defines the list of attributes that describe a given type of object. For example, let's say that all printer objects are defined by name, PDL type and speed attributes. This list of attributes comprises the schema for the object class "printers". The schema is customizable, meaning that the attributes that define an object class can be modified.
Schema Master - The schema master FSMO role is the DC responsible for performing updates to the directory schema. This DC is the only one that can process updates to the directory schema. Once the schema update is complete, it is replicated from the schema master to all other DCs in the directory. There is only one schema master per directory.
 SCSI (Small Computer Systems Interface) - Prounounced "Scuzzy", SCSI is an alternative to the IDE interface for connecting mass storage devices. SCSI is faster than IDE, however, because of its cost SCSI devices are most commonly found in servers and high-end workstations. SCSI devices, such as hard drives, tape drives, and CD-ROM drives, plug into a SCSI controller internally or externally, and multiple devices can be configured in a chain. In order for the SCSI bus to work correctly, the last device on any SCSI chain must be terminated. Some SCSI devices are self-terminating, while others can be terminated using jumpers or a resistor that plugs into the end of the cable or device. Each device on a SCSI chain must receive its own SCSI ID including the controller which is usually preset to ID 7. Newer SCSI standards support up to 16 devices in a chain. SCSI (Small Computer Systems Interface) - Prounounced "Scuzzy", SCSI is an alternative to the IDE interface for connecting mass storage devices. SCSI is faster than IDE, however, because of its cost SCSI devices are most commonly found in servers and high-end workstations. SCSI devices, such as hard drives, tape drives, and CD-ROM drives, plug into a SCSI controller internally or externally, and multiple devices can be configured in a chain. In order for the SCSI bus to work correctly, the last device on any SCSI chain must be terminated. Some SCSI devices are self-terminating, while others can be terminated using jumpers or a resistor that plugs into the end of the cable or device. Each device on a SCSI chain must receive its own SCSI ID including the controller which is usually preset to ID 7. Newer SCSI standards support up to 16 devices in a chain.
SDRAM - Stands for Synchronous DRAM and has replaced regular DRAM because of its faster speeds.Whilst DRAM has an asynchronous interface, meaning that it reacts immediately to changes in its control inputs, SDRAM has a synchronous interface, meaning that it waits for a clock pulse before responding to its control inputs. The clock is used to drive an internal finite state machine that can pipeline incoming commands. This allows the chip to have a more complex pattern of operation than plain DRAM. SDRAM is probably the most commonly used memory type today.
SDR SDRAM - Stands for Single Data Rate SDRAM, a type of computer memory. The term is used to contrast with Double Data Rate SDRAM, or DDR SDRAM, but since single data rate SDRAM was the only sort available when SDRAM was introduced, it is more commonly called "ordinary SDRAM" or something similar, rather than "SDR SDRAM".
 Secure Digital Cards - Secure Digital (SD) cards are the most commonly used format today after displacing a similar type by SmartMedia. SD cards come in 2 types: SD and SDIO. Both are identical looking so you need to check with the manual or manufacturer of your device to find which to use. SD cards are smaller than CompactFlash, but come in 2 even smaller sizes: MiniSD and MicroSD are smaller versions that are commonly used in cell phones. Secure Digital Cards - Secure Digital (SD) cards are the most commonly used format today after displacing a similar type by SmartMedia. SD cards come in 2 types: SD and SDIO. Both are identical looking so you need to check with the manual or manufacturer of your device to find which to use. SD cards are smaller than CompactFlash, but come in 2 even smaller sizes: MiniSD and MicroSD are smaller versions that are commonly used in cell phones.
Seek Time - This is the amount of time it takes for a hard drive's head to move between cylinders and land on a particular track.
SET (Secure Electronic Transaction) - SET gives users a digital certificate and a transaction is conducted and verified using a combination of digital certificates and digital signatures among the parties involved in the transaction in such a way that ensures privacy and confidentiality.
SFTP (Secure File Transfer Protocol) - Similar to standard FTP but performs operations over an encrypted link (SSH) and is thus said to be secure. You can't use a standard FTP client to talk to an SFTP server, nor can you connect to an FTP server with a client that supports only SFTP. SFTP was written independently of FTP and is a completely separate protocol.
SHA (Secure Hash Algorithm - A family of related cryptographic hash functions. The most commonly used function in thegroup, SHA-1, is used in a large variety of security applications and protocols, including IPSec, TLS, SSL, PGP, SSH, and S/MIME. SHA-1 is considered to be the successor to MD5, an earlier, widely-used hash function. The SHA algorithms were designed by the National Security Agency (NSA) and published as a US government standard.
SIP – Stands for Session Initiation Protocol and is a signaling protocol, widely used for controlling multimedia communication sessions such as voice and video calls over Internet Protocol (IP). Other feasible application examples include video conferencing, streaming multimedia distribution, instant messaging, presence information and online games. The protocol can be used for creating, modifying and terminating two-party (unicast) or multiparty (multicast) sessions consisting of one or several media streams. The modification can involve changing addresses or ports, inviting more participants, adding or deleting media streams, etc.
Sites - Sites are used to define the boundaries of high-speed links on a network containing Active Directory Servers. Sites are based on IP subnets and are defined as a "well-connected subnet or subnets".
 Smart Card - The term smart card has been used to describe a class of credit card-sized devices with varying capabilities, however, they are most commonly used for identification, building entry, and financial transactions. The card is typically inserted into a reader device which reads the contents of the ICC chip in the card. It is the ICC (Integrated Circuit Card) that is of most interest to the personal computer because it is able to perform more sophisticated operations such as digital signature and key exchange. Newer operating systems are supporting smart card authentication. Smart Card - The term smart card has been used to describe a class of credit card-sized devices with varying capabilities, however, they are most commonly used for identification, building entry, and financial transactions. The card is typically inserted into a reader device which reads the contents of the ICC chip in the card. It is the ICC (Integrated Circuit Card) that is of most interest to the personal computer because it is able to perform more sophisticated operations such as digital signature and key exchange. Newer operating systems are supporting smart card authentication.
Smart Jack – This is a network connection device that is used to connect your internal network to an external service provider network. The device handles all of the code and protocol differences between the two networks and is often the actual demarcation point between the two service entities. network. The device handles all of the code and protocol differences between the two networks and is often the actual demarcation point between the two service entities.
SMF (Single-Mode Fiber) - A single-mode optical fiber is an optical fiber in which only the lowest order bound mode can propagate at the wavelength of interest. Single mode fibers are best at maintaining the signal of each light pulse over longer distances and exhibit no dispersion caused by multiple modes. The result is that this type offers a higher bandwidth in comparison with multi-mode fibers (MMF).
 SMTP (Simple Mail Transfer Protocol) - SMTP is a member of the TCP/IP protocol suite and is responsible for the delivery of mail between mail servers. SMTP is also used in most cases to deliver mail from the email client to the mail server. SMTP does not handle the transfer of mail from the mail server to the client (i.e. Outlook) - POP3 or IMAP is responsible for that. SMTP uses port 25. SMTP (Simple Mail Transfer Protocol) - SMTP is a member of the TCP/IP protocol suite and is responsible for the delivery of mail between mail servers. SMTP is also used in most cases to deliver mail from the email client to the mail server. SMTP does not handle the transfer of mail from the mail server to the client (i.e. Outlook) - POP3 or IMAP is responsible for that. SMTP uses port 25.
Smurf Attack - This is a type of denial-of-service attack that floods a target system via spoofed broadcast ping messages in an attempt to cause massive network traffic. To accomplish this, the attacker sends ICMP echo packets to broadcast addresses of vulnerable networks with a forged source address pointing to the target (victim) of the attack. All the systems on these networks reply to the victim with ICMP echo replies which will overload it. These types of attacks are very easy to prevent, and as a result, they are no longer very common.
SNAT – Secure Network Address Translation an extension of the standard Network Address Translation (NAT) service. SNAT is done through one to one IP address translation of one internal IP address to one external IP address where NAT is effectively one external address to many internal IP addresses.
SNMP (Simple Network Management Protocol) - Part of the TCP/IP suite of protocols, SNMP is a protocol used by network hosts to exchange information used in the management of networks. SNMP network management is based on the client and server model. Each managed host runs a process called an agent. The agent is a server process that maintains the Management Information Base (MIB) database for the host. SNMP is used to report usage, statistics, errors, performance metrics and other information from a SNMP device to the agent.
Social Engineering - Social engineering describes various types of deception used for the purpose of information gathering, fraud, or computer system access. Phishing, a form of social engineering, is the fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication such as email, chat, or instant messaging.
SPX (Sequenced Packet Exchange) - A Novell networking protocol that provides guaranteed in-sequence delivery of packets on Novell Netware networks. SPX runs in conjuction with IPX and provides a layer of error correction.
SONET (Synchronous Optical NETwork) - SONET and SDH are a set of related standards for synchronous data transmission over fiber optic networks. SONET is the United States version of the standard and SDH is the international version. SONET defines a base rate of 51.84 Mbps and a set of multiples of the base rate known as "Optical Carrier levels." (OCx). Speeds approaching 40 gigabits per second are possible.
SQL (Structured Query Language) - Pronounced "Sequel", SQL is a query language used for accessing and modifying information in a relational database. The language was first created by IBM in 1975. The most popular SQL database servers are Oracle, MySQL, and Microsoft SQL Server. SQL Tutorial
SRAM - Stands for Static Random Access Memory. SRAM is faster and more reliable than Dynamic Random Access Memory (DRAM) and it doesn’t have to be constantly refreshed. Uses a lot of power. Used in old IBM XT machines and was limited to 256K per chip.
SSH (Secure Shell) - Developed by SSH Communications Security Ltd., SSH is a program and network protocol used to remotely access a computer, login, and execute commands on it. It is very similar to Telnet, but is better because it provides secure encrypted communications while Telnet has been found to be exploitable and insecure. SSH uses public-key cryptography to authenticate the remote computer and utilizes port 22.
SSI (Server Side Includes) - SSI provides a way to create templates for static elements of HTML web pages. In other words, elements that are the same across all of pages of a web site such as menus, sidebars, etc. The advantage of using includes is that you don't have to update all of the pages of the site when an element in your include file changes - you just have to update the 1 include file. SSI pages are typically called using the following syntax: . The pages of the web site should be given the .shtml or shtm extension and the include files use the .html extension.
SSL (Secure Sockets Layer) - SSL is a protocol developed by Netscape used to provide secure transmission of private documents over the internet. It is most commonly used for e-commerce applications such as the creating secure HTTP pages (HTTPS) that protect confidential information such as credit card numbers during online purchases. SSL uses the public- and private-key encryption system, which includes the use of a digital certificate.
SSL VPN (Secure Sockets Layer virtual private network) - This is a VPN that runs on SSL and is accessible via https over a web browser . It allows users to establish secure remote access sessions from virtually any Internet connected browser. Unlike a traditional VPN, this method does not require the use of IPSec. The benefit of this solution is that it allows clients to access a corporate network from nearly anywhere which is not practical with a typical VPN. . It allows users to establish secure remote access sessions from virtually any Internet connected browser. Unlike a traditional VPN, this method does not require the use of IPSec. The benefit of this solution is that it allows clients to access a corporate network from nearly anywhere which is not practical with a typical VPN.
Star Topology - Star networks are one of the most common network topologies used today. In a star topology, the workstations, fileservers, printers etc. are attached via drop cables to a central hub or switch. This central hub rebroadcasts all transmissions received from any peripheral node to all peripheral nodes on the network. Should this central hub fail, devices on the network will not be able to communicate with each other, however, the failure of a node connected to the hub will not affect communications between the remaining nodes.
 STP1 (Shielded Twisted Pair) - This type of cable is the same as unshielded twisted pair (UTP), except that it has shielding around it to provide more protection against electromagnetic interference (EMI). STP1 (Shielded Twisted Pair) - This type of cable is the same as unshielded twisted pair (UTP), except that it has shielding around it to provide more protection against electromagnetic interference (EMI).
STP2 (Spanning-Tree Protocol) - STP allows duplicate switched/bridged paths without incurring the latency effects of loops in the network. The Spanning-Tree Algorithm, implemented by the Spanning-Tree Protocol, prevents loops by calculating stable spanning-tree network topology. When creating a fault-tolerant network, a loop-free path must exist between all nodes in the network The Spanning-Tree Algorithm is used to calculate a loop-free paths. Spanning-tree frames, called bridge protocol data units (BPDUs), are sent and received by all switches in the network at regular intervals and are used to determine the spanning-tree topology.
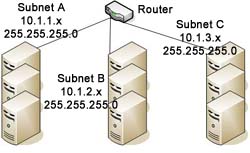 Subnet - A subnet is a logical grouping of connected network devices. Network designers use subnets as a way to divide networks into logical segments for greater ease of administration, improved security, and better performance. In IP networking, nodes on a subnet share a contiguous range of IP address numbers. A number called a subnet mask blocks out a portion of an IP address and is used to differentiate between the host ID and network ID. Subnet - A subnet is a logical grouping of connected network devices. Network designers use subnets as a way to divide networks into logical segments for greater ease of administration, improved security, and better performance. In IP networking, nodes on a subnet share a contiguous range of IP address numbers. A number called a subnet mask blocks out a portion of an IP address and is used to differentiate between the host ID and network ID.
Subnetting 123
Subnetting Confusion
Subnet Calculator
 Switch - A switch is a network device that filters and forwards packets between LAN segments and ensures that data goes straight from its origin to its proper destination. Switches remember the address of every node on the network, and anticipate where data needs to go. It only operates with the computers on the same LAN. This reduces competition for bandwidth between devices on the network. Switch - A switch is a network device that filters and forwards packets between LAN segments and ensures that data goes straight from its origin to its proper destination. Switches remember the address of every node on the network, and anticipate where data needs to go. It only operates with the computers on the same LAN. This reduces competition for bandwidth between devices on the network.
Syn Flooding - In a SYN Flood attack, the client uses an unavailable IP address so that the server's SYN-ACK message never reaches its destination. This results in a "half-open" connection. The attacker floods the server with these types of requests making the server unable to respond to new valid requests.
Synchronous - In telecommunication signaling within a network or between networks, synchronous signals are those that occur at the same clock rate when all clocks are based on a single reference clock. In program-to-program communication, synchronous communication requires that each end of an exchange of communication respond in turn without initiating a new communication. A typical activity that might use a synchronous protocol would be a transmission of files from one point to another. As each transmission is received, a response is returned indicating success or the need to resend. Each successive transmission of data requires a response to the previous transmission before a new one can be initiated.
|
TACACS+ (Terminal Access Controller Access-Control System) - TACACS+ is a proprietary Cisco security application that provides centralized validation of users attempting to gain access to a router or network access server. The TACACS+ protocol provides authentication between the network access server and the TACACS+ daemon, and it ensures confidentiality because all protocol exchanges between a network access server and a TACACS+ daemon are encrypted. Whereas RADIUS combines authentication and authorization in a user profile, TACACS+ separates the two operations. Another difference is that TACACS+ uses the Transmission Control Protocol (TCP) while RADIUS uses the User Datagram Protocol (UDP).
TCP (Transmission Control Protocol) - TCP is a transport layer protocol used in conjunction with the Internet Protocol (IP). TCP allows applications to create connections with one another and stream data. TCP breaks data into manageable packets and tracks information such as source and destination of packets. It is able to reroute packets and is responsible for guaranteed delivery of the data. More information...
Telnet - Telnet is a protocol that allows you to connect to remote computers over the Internet. There is a telnet server on the remote host, which the telnet client negotiates with to establish a connection. Once connected, the client becomes a virtual terminal, and allows you to interface with the host computer via command line from your computer. In most cases, you'll be asked to log into the remote system. This usually requires an account on that host. Telnet uses port 23. Because of security issues with Telnet, Secure Shell (SSH) is replacing becoming the new standard.
TFTP (Trivial File Transfer Protocol) - TFTP is a "Lite" version of FTP and can be used for basic file transfer operations. It uses the User Datagram Protocol (UDP) and provides no security features. It is most often used by servers to boot diskless workstations, X-terminals, and routers.
TIFF (Tagged Image File Format) - Developed by Aldus for use with PostScript printing, TIFF files are uncompressed bitmap images commonly used in desktop publishing, faxing, 3-D applications, and medical imaging applications. A plug-in is required to view TIFF images in a browser. TIFF images typically use the .tif file extension.
TLS - Transport Layer Security is a cryptographic protocol that provides security for communications over networks such as the Internet. TLS and SSL encrypt the segments of network connections at the Transport Layer end-to-end. Several versions of the protocols are in wide-spread use in applications like web browsing, electronic mail, Internet faxing, instant messaging and voice-over-IP (VoIP). such as the Internet. TLS and SSL encrypt the segments of network connections at the Transport Layer end-to-end. Several versions of the protocols are in wide-spread use in applications like web browsing, electronic mail, Internet faxing, instant messaging and voice-over-IP (VoIP).
Token Ring - Token Ring is an older standard that isn't very widely used anymore as most have migrated to some form of Ethernet or other advanced technology. Ring topologies can have transmission rates of either 4 or 16mbps. Token passing is the access method used by token ring networks, whereby, a 3bit packet called a token is passed around the network. A computer that wishes to transmit must wait until it can take control of the token, allowing only one computer to transmit at a time. This method of communication aims to prevent collisions. Token Ring networks use multistation access units (MSAUs) instead of hubs on an Ethernet network.
Token Ring/IEEE 802.5
Traceroute - A command-line troubleshooting tool that enables you to view the route to a specified host. This will show how many hops the packets have to travel and how long it takes. In Windows operating systems, the command used is "tracert".
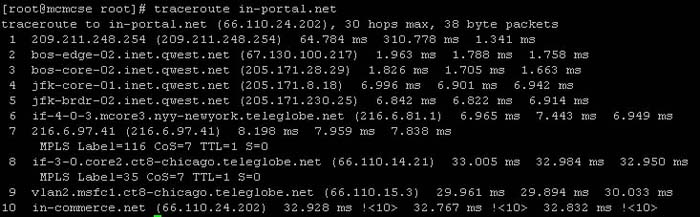
Traffic Shaping (also known as "packet shaping" or ITMPs: Internet Traffic Management Practices) is the control of computer network traffic in order to optimize or guarantee performance, increase/decrease latency, and/or increase usable bandwidth by delaying packets that meet certain criteria. More specifically, traffic shaping is any action on a set of packets (often called a stream or a flow) which imposes additional delay on those packets such that they conform to some predetermined constraint (a contract or traffic profile).Traffic shaping provides a means to control the volume of traffic being sent into a network in a specified period (bandwidth throttling), or the maximum rate at which the traffic is sent (rate limiting), or more complex criteria such as GCRA. This control can be accomplished in many ways and for many reasons; however traffic shaping is always achieved by delaying packets. Traffic shaping is commonly applied at the network edges to control traffic entering the network, but can also be applied by the traffic source (for example, computer or network cardhttp://en.wikipedia.org/wiki/Traffic_shaping - cite_note-2) or by an element in the network. Traffic policing is the distinct but related practice of packet dropping and packet marking.
Trojan Horse - A Trojan is a type of file that appears to do one thing, but in reality does another. A Trojan can be a file that operates in an expected way, but also has a secret operation that subverts security. Once a Trojan is installed, it can perform a wide variety of destructive tasks and/or provide secure information to the attacker.
Trunking - VLANs are local to each switch's database , and VLAN information is not passed between switches. Trunk links provide VLAN identification for frames traveling between switches. The VLAN trunking protocol (VTP) is the protocol that switches use to communicate among themselves about VLAN configuration. , and VLAN information is not passed between switches. Trunk links provide VLAN identification for frames traveling between switches. The VLAN trunking protocol (VTP) is the protocol that switches use to communicate among themselves about VLAN configuration.
|
UDP (User Datagram Protocol) - UDP is a core component of the Internet Protocol suite. Like TCP, UDP is used with IP, however, UDP is connectionless and does not guarantee reliable communication; the application itself must process any errors and check for reliable delivery. It is used in place of TCP when a reliable delivery is not required such as with streaming audio and video, DNS, online gaming, VOIP, SNMP, RIP, etc.
Unicast - the sending of information packets to a single network node. This type of network transmission is used where a private or unique resource such as media servers are being requested for two way connections that are needed to complete the network communication. So in the media server example, a client system may make the request for streaming content from the single source and the responding system may leverage unicast as part of the response to the session request to deliver the content. example, a client system may make the request for streaming content from the single source and the responding system may leverage unicast as part of the response to the session request to deliver the content.
 URL (Uniform Resource Locator) - As the name indicates, a URL is an address used to give the location of a resource on the web. The first part is the ‘service descriptor’ which identifies the protocol being used (in the diagram it is HTTP). The ‘//’ indicates the start of path (the root directory) which is followed by the domain name. The remainder of the address is the directory path on the server that specifies the location of the file to be fetched. You may have noticed that when you visit a domain, the complete path is not displayed. For example, if you visit our home page at http://www.mcmcse.com, there is no file specified after the domain name. URL (Uniform Resource Locator) - As the name indicates, a URL is an address used to give the location of a resource on the web. The first part is the ‘service descriptor’ which identifies the protocol being used (in the diagram it is HTTP). The ‘//’ indicates the start of path (the root directory) which is followed by the domain name. The remainder of the address is the directory path on the server that specifies the location of the file to be fetched. You may have noticed that when you visit a domain, the complete path is not displayed. For example, if you visit our home page at http://www.mcmcse.com, there is no file specified after the domain name.
 USB (Universal Serial Bus) - A plug-and-play interface between a computer and peripherals (such as keyboards, scanners, printers, digital cameras, etc). In some situations, it can also be used to network 2 computers USB (Universal Serial Bus) - A plug-and-play interface between a computer and peripherals (such as keyboards, scanners, printers, digital cameras, etc). In some situations, it can also be used to network 2 computers directly together. USB devices are "hot-swappable" which means that a new device can be added or removed without having to shut down the computer. USB 2.0 can transmit data at speeds up to 480Mbps. When a lot of USB devices need to be connected to a computer, a USB hub can be used to handle the extra connections. directly together. USB devices are "hot-swappable" which means that a new device can be added or removed without having to shut down the computer. USB 2.0 can transmit data at speeds up to 480Mbps. When a lot of USB devices need to be connected to a computer, a USB hub can be used to handle the extra connections.
USB Flash Drive - See Flash Drives
 UTP (Unshielded Twisted Pair) - It is a cable type that consists of two or more insulated conductors in which each pair of conductors are twisted around each other. Category 1 UTP cables are used for telephony connections. Category 3 and higher are used for Ethernet LAN connections. UTP is inexpensive and easy to work with. UTP (Unshielded Twisted Pair) - It is a cable type that consists of two or more insulated conductors in which each pair of conductors are twisted around each other. Category 1 UTP cables are used for telephony connections. Category 3 and higher are used for Ethernet LAN connections. UTP is inexpensive and easy to work with.
Category 5 / 5E & Cat 6 Cabling Tutorial and FAQ's
|
|
Virtual Memory - Also referred to as "swap space", Virtual Memory is free hard drive space that can be used as extra memory for a computer. Virtual memory is much slower than physical memory (RAM).
Virus - A Computer Virus is a program that can copy itself and infect a computer without the permission or knowledge of the user. A Computer Virus has 2 major characteristics: the ability to replicate itself, and the ability to attach itself to another computer file. Every file or program that becomes infected can also act as a Virus itself, allowing it to spread to other files and computers. The term "computer virus" is often used incorrectly as a catch-all phrase to include all types of Malware such as Computer Worms, Trojan Horses, Spyware, Adware, and Rootkits. There are many different anti-virus programs available to prevent and remove viruses. Since new threats are created almost constantly, it is important to keep the virus definition files updated for your software.
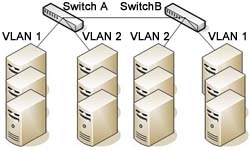 VLAN (Virtual Local Area Network) - A VLAN is a logical grouping of devices or users. These devices or users can be grouped by function, department application and so on, regardless of their physical segment location. VLANs create separate broadcast domains in a switched network. Frame tagging at layer 2 does this. Frame tagging is a gaining recognition as the standard for implementing VLANs, and is recognized by IEEE 802.1q. Frame tagging uniquely assigns a VLAN ID to each frame. This identifier is understood and examined by each switch prior to any broadcasts or transmissions to other switches, routers, and end-stations devices. VLAN (Virtual Local Area Network) - A VLAN is a logical grouping of devices or users. These devices or users can be grouped by function, department application and so on, regardless of their physical segment location. VLANs create separate broadcast domains in a switched network. Frame tagging at layer 2 does this. Frame tagging is a gaining recognition as the standard for implementing VLANs, and is recognized by IEEE 802.1q. Frame tagging uniquely assigns a VLAN ID to each frame. This identifier is understood and examined by each switch prior to any broadcasts or transmissions to other switches, routers, and end-stations devices.
VNC (Virtual Network Computing) - VNC makes it possible to interact with a computer from any computer or mobile device on the Internet. Unlike Microsoft's RDP, VNC offers cross-platform support allowing remote control between different types of computers. Popular uses for this technology include remote technical support and accessing files on one's work computer from one's home computer, or vice versa.
VOIP (Voice Over Internet Protocol) - Also known as Internet Telephony, VOIP is the technology that allows voice traffic to be transmitted and routed over a data network using the Internet Protocol. The advantage of VOIP is that it is low cost (in some cases free) in comparison to using tradition POTS (Plain Old Telephone Systems) for voice communications. Companies such as Vonage and Comcast Cable are currently offering VOIP phone services and Skype is a freeware program that provides free long distance communications with other Skype users. Systems) for voice communications. Companies such as Vonage and Comcast Cable are currently offering VOIP phone services and Skype is a freeware program that provides free long distance communications with other Skype users.
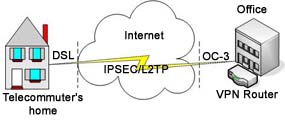 VPN (Virtual Private Network) - A VPN is a network that uses a public telecommunication infrastructure, such as the Internet, to provide remote offices or individual users with secure access to their organization's network. A VPN works by using the shared public infrastructure while maintaining privacy through security procedures and tunneling protocols such as the Layer Two Tunneling Protocol (L2TP) or PPTP. In effect, the protocols, by encrypting data at the sending end and decrypting it at the receiving end, send the data through a "tunnel" that cannot be "entered" by data that is not properly encrypted. VPN (Virtual Private Network) - A VPN is a network that uses a public telecommunication infrastructure, such as the Internet, to provide remote offices or individual users with secure access to their organization's network. A VPN works by using the shared public infrastructure while maintaining privacy through security procedures and tunneling protocols such as the Layer Two Tunneling Protocol (L2TP) or PPTP. In effect, the protocols, by encrypting data at the sending end and decrypting it at the receiving end, send the data through a "tunnel" that cannot be "entered" by data that is not properly encrypted.
VRAM - Video RAM. This type of memory is used on video adapters, and is dual-ported, meaning that it can be accessed by two devices simultaneously. This allows the monitor to access the memory for screen updates, while at the same time allowing the graphics processor to provide new data. VRAM is no longer to be found on new devices; it was rapidly superseded by SGRAM and then DDR-SDRAM.
VRML (Virtual Reality Modeling Language) - VRML allows the display of 3-D vector objects within a web browser
W3C (World Wide Web Consortium) - The mission of the W3C is to lead the World Wide Web to its full potential by developing protocols and guidelines that ensure long-term growth for the Web. W3C primarily pursues its mission through the creation of Web standards and guidelines. Since 1994, W3C has published more than ninety such standards, called W3C Recommendations. W3C also engages in education and outreach, develops software, and serves as an open forum for discussion about the Web.
World Wide Web Consortium
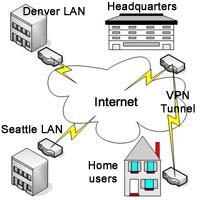 WAN (Wide Area Network) - A computer network that spans a relatively large geographical area. Typically, a WAN consists of two or more local-area networks WAN (Wide Area Network) - A computer network that spans a relatively large geographical area. Typically, a WAN consists of two or more local-area networks (LANs). Computers connected to a wide-area network are often connected through public networks, such as the telephone system, leased lines (ISDN), satellite, microwave, or other connection method. The connected LANS can be on another in a building, or as far away as in another country. The largest WAN in existence is the Internet. (LANs). Computers connected to a wide-area network are often connected through public networks, such as the telephone system, leased lines (ISDN), satellite, microwave, or other connection method. The connected LANS can be on another in a building, or as far away as in another country. The largest WAN in existence is the Internet.
There are a wide number of WAN connection types and speeds including DSL, broadband cable, T carrier lines (eg. T1), satellite and many others.
WAP (Wireless Access Point) - A Wireless Access Point is a radio frequency transceiver which allows your wireless devices to connect to a network. A wireless access point will support up to 32 wireless devices. The table below shows the various wireless standards:

| Standard | Speed | Distance | Frequency |
| 802.11a | 54 mbps | 100 ft | 5 GHz |
| 802.11b | 11 mbps | 300 ft | 2.4 GHz |
| 802.11g | 54 mbps | 300 ft | 2.4 GHz |
| 802.11n | 540 mbps | 600 ft | 5 GHz and/or 2.4 GHz |
Windows Domain - The term domain in Windows environments refers to a logical group of computers running versions of the Microsoft Windows operating system that share a central directory database . Currently, this database is known as Active Directory on Windows 2003 domain controllers. Domains do not define the physical makeup of a LAN or WAN, but rather they define security and access. Domains centralize user and computer (client) access to network resources via user accounts stored in the Active Directory database on the domain controllers. Do not confuse this term with Domain Names on the internet. . Currently, this database is known as Active Directory on Windows 2003 domain controllers. Domains do not define the physical makeup of a LAN or WAN, but rather they define security and access. Domains centralize user and computer (client) access to network resources via user accounts stored in the Active Directory database on the domain controllers. Do not confuse this term with Domain Names on the internet.
WINS (Windows Internet Naming System) - Microsoft's definition of WINS is "An enhanced NetBIOS Name Server (NBNS) designed by Microsoft to eliminate broadcast traffic associated with the B-node implementation of NetBIOS over TCP/IP. It is used to register NetBIOS names and resolve them to IP addesses for both local and remote hosts." WINS is a proprietary Microsoft name server and with Windows 2000, Microsoft introduced dynamic DNS which has largely replaced the need for WINS. The fact that DNS is the de facto standard on the internet is a large part of the reason that WINS is disappearing.
 WLAN (Wireless Local Area Network) - A WLAN is local area network available through a wireless connection using the 802.11 family of standards. The wireless connections utilize spread-spectrum technology based on radio waves to enable communication between devices in a limited area. WLAN (Wireless Local Area Network) - A WLAN is local area network available through a wireless connection using the 802.11 family of standards. The wireless connections utilize spread-spectrum technology based on radio waves to enable communication between devices in a limited area.
WML (Wireless Markup Language) - Formerly called Handheld Devices Markup Languages (HDML), WML is a markup language that allows the text portions of Web pages to be presented on cell phones and PDAs via wireless access. WML is part of the Wireless Application Protocol (WAP). There are filter programs available that can convert HTML pages into this format.
Workgroup - A workgroup is a logical collection of computers identified by a unique name. Members of the workgroup can see and access resources shared by other computers within the group. Unlike a domain configuration, each computer in the workgroup manages its own security rather than having centralized accounts and security managed by a domain controller running Active Directory. Workgroups are only manageable for very small peer-to-peer networks.
Worm - Worms are stand alone programs that do not need other programs in order to replicate themselves like a virus which relies on users to inadvertently spread it. Viruses and Worms can be prevented by installing anti-virus software which can be run on servers, clients, firewalls and other devices.
WRAM (Window Random Access Memory) - Despite its name, this type of memory has nothing to do with Windows OS. It is an updated version of VRAM in that data can be read from the memory chips whilst new data is written into them - VRAM could only do either a read or a write. WRAM is no longer to be found on new devices; for graphics cards, it was rapidly superseded by SGRAM and then DDR-SDRAM.
|
X.25 - In 1976 X.25 was recommended as the desired protocol by the International Consultative Committee for Telegraphy and Telephony (CCITT) called the International Telecommunication Union (ITU) since 1993. X.25 is a packet switched data network protocol which defines an international recommendation for the exchange of data as well as control information between a user device (host), called Data Terminal Equipment (DTE) and a network node, called Data Circuit Terminating Equipment (DCE). In other words, this protocol was used for wide area networks using the phone or ISDN system as the networking hardware. The X25 standard consists of 3 layers as follows: The packet layer, the link layer, and the network (or packet) layer. These three levels conform to the lower three layers of the OSI seven-layer reference model for open system interconnection. X.25 networks are still in use throughout the world, although mainly in developing countries. Layer 2 technologies such as frame relay, ISDN, ATM, ADSL, POS, and the layer 3 Internet Protocol have largely replaced the need for X.25 elsewhere. using the phone or ISDN system as the networking hardware. The X25 standard consists of 3 layers as follows: The packet layer, the link layer, and the network (or packet) layer. These three levels conform to the lower three layers of the OSI seven-layer reference model for open system interconnection. X.25 networks are still in use throughout the world, although mainly in developing countries. Layer 2 technologies such as frame relay, ISDN, ATM, ADSL, POS, and the layer 3 Internet Protocol have largely replaced the need for X.25 elsewhere.
X.25 Overview
XHTML (eXtensible HyperText Markup Language) - The evolution of HTML has essentially stopped. Instead, HTML is being replaced by a new language, called XHTML. XHTML is in many ways similar to HTML, but is designed to work with the new eXtensible Markup Language, or XML, that will soon serve as the core language for designing all sorts of new Web applications, in which XHTML will be only one of many "languages". XHTML is designed to work with these other languages, so that different documents, in different languages, can be easily mixed together. has essentially stopped. Instead, HTML is being replaced by a new language, called XHTML. XHTML is in many ways similar to HTML, but is designed to work with the new eXtensible Markup Language, or XML, that will soon serve as the core language for designing all sorts of new Web applications, in which XHTML will be only one of many "languages". XHTML is designed to work with these other languages, so that different documents, in different languages, can be easily mixed together.
XML (eXtensible Markup Language) - XML is a standard for creating markup languages which describe the structure of data. It is not a fixed set of elements like HTML, but rather, it is like a language for describing languages. XML enables authors to define their own tags. XML is a formal specification of the World Wide Web Consortium.
Official Site
XML Tutorial
XSL (eXtensible Stylesheet Language) - XSL and is a language for expressing style sheets. An XSL style sheet is, like with CSS, a file that describes how to display an XML document of a given type. Separating the document's content and the document's styling information allows displaying the same document on different media (like screen, paper, cell phone), and it also enables users to view the document according to their preferences and abilities, just by modifying the style sheet.
|
Ymodem - A protocol for transferring files during direct dial-up communications. It is a variation of the Xmodem file transfer protocol that includes the following enhancements: the ability to transfer information in 1-kilobyte (1,024-byte) blocks, the ability to send multiple files (batch file transmission), cyclical redundancy checking (CRC), and the ability to abort transfer by transmitting two CAN (cancel) characters in a row. protocol that includes the following enhancements: the ability to transfer information in 1-kilobyte (1,024-byte) blocks, the ability to send multiple files (batch file transmission), cyclical redundancy checking (CRC), and the ability to abort transfer by transmitting two CAN (cancel) characters in a row.
|
 ZIF (Zero Insertion Force) - A ZIF Socket is The ZIF socket has a small lever on the side of it which is lifted to release the CPU or allow one to be inserted. Once the CPU is in place, the lever is pushed down and the electrical contacts grip the pins on the CPU clamping it into place. This socket type was invented to prevent damage to the CPU caused by the force required to press the CPU into place. Previous designs also had a risk of bending the pins on the processor ZIF (Zero Insertion Force) - A ZIF Socket is The ZIF socket has a small lever on the side of it which is lifted to release the CPU or allow one to be inserted. Once the CPU is in place, the lever is pushed down and the electrical contacts grip the pins on the CPU clamping it into place. This socket type was invented to prevent damage to the CPU caused by the force required to press the CPU into place. Previous designs also had a risk of bending the pins on the processor when attempting to push it into place. when attempting to push it into place.
 ZIP Drive - Introduced by Iomega in 1994, ZIP drives are internal or external storage devices that used removable ZIP disks to store data. Later versions of ZIP disks could store up to 750mb of data. Internal ZIP drives came with either an IDE or SCSI interface, while external drives came with either a parallel, SCSI, or USB (later years) interface. The external versions were popular due to their portability. The original Zip drive had a data transfer rate of about 1 megabyte/second and a seek time of 28 milliseconds on average, compared to a standard 1.44 MB floppy's 500 kbit/s (62.5 kB/s) transfer rate and several-hundred millisecond average seek time. The ZIP drive's popularity was fleeting as larger capacity options such as CD/DVD burners, flash drives, and other technologies have made them almost obselete. ZIP Drive - Introduced by Iomega in 1994, ZIP drives are internal or external storage devices that used removable ZIP disks to store data. Later versions of ZIP disks could store up to 750mb of data. Internal ZIP drives came with either an IDE or SCSI interface, while external drives came with either a parallel, SCSI, or USB (later years) interface. The external versions were popular due to their portability. The original Zip drive had a data transfer rate of about 1 megabyte/second and a seek time of 28 milliseconds on average, compared to a standard 1.44 MB floppy's 500 kbit/s (62.5 kB/s) transfer rate and several-hundred millisecond average seek time. The ZIP drive's popularity was fleeting as larger capacity options such as CD/DVD burners, flash drives, and other technologies have made them almost obselete.
Iomega's official site
zombie - A computer attached to a network that has had its security compromised and is remotely controlled for another purpose. Usually, zombie computers are used as a launching point for another attack, or the distribution of SPAM. are used as a launching point for another attack, or the distribution of SPAM.
|
|
|
|




 BIOS - BIOS stands for Basic Input/Output System and is software that manages hardware and allows the operating system to talk to the various components. The BIOS is also responsible for allowing you to control your computer's hardware settings, for booting up the machine when you turn on the power or hit the reset button and various other system functions. The BIOS software lives on a ROM IC on the motherboard known as a Complementary Metal Oxide Semiconductor(CMOS). People often incorrectly refer to the BIOS setup utility as CMOS, however, CMOS is the name of the physical location that the BIOS settings are stored in. The term BIOS is typically used to refer to the system BIOS, however, various other components such as video adapters and hard drives can have their own BIOSes hardwired to them.
BIOS - BIOS stands for Basic Input/Output System and is software that manages hardware and allows the operating system to talk to the various components. The BIOS is also responsible for allowing you to control your computer's hardware settings, for booting up the machine when you turn on the power or hit the reset button and various other system functions. The BIOS software lives on a ROM IC on the motherboard known as a Complementary Metal Oxide Semiconductor(CMOS). People often incorrectly refer to the BIOS setup utility as CMOS, however, CMOS is the name of the physical location that the BIOS settings are stored in. The term BIOS is typically used to refer to the system BIOS, however, various other components such as video adapters and hard drives can have their own BIOSes hardwired to them. BNC (Bayonet Neill Concelman) - Sometimes incorrectly referred to as a "British Naval Connector", this connector named after its inventor has found uses with both broadcast television equipment and computer networks. Nowadays, it is most commonly seen as the connector found on coaxial cable used in homes. With regards to networking, this connector was used on early 10Base-2 (Thinnet) Ethernet networks. It has a center pin connected to the center cable conductor and a metal tube connected to the outer cable shield. A rotating ring outside the tube locks the cable to the female connector.
BNC (Bayonet Neill Concelman) - Sometimes incorrectly referred to as a "British Naval Connector", this connector named after its inventor has found uses with both broadcast television equipment and computer networks. Nowadays, it is most commonly seen as the connector found on coaxial cable used in homes. With regards to networking, this connector was used on early 10Base-2 (Thinnet) Ethernet networks. It has a center pin connected to the center cable conductor and a metal tube connected to the outer cable shield. A rotating ring outside the tube locks the cable to the female connector.
 AGP - Short for Accelerated Graphics Port, an interface specification developed by Intel Corporation. AGP is based on PCI, but is designed especially for the throughput demands of 3-D graphics. Rather than using the PCI bus for graphics data, AGP introduces a dedicated point-to-point channel so that the graphics controller can directly access main memory. The AGP channel is 32 bits wide and runs at 66 MHz. It can achieve throughput up to 266Mbps.
AGP - Short for Accelerated Graphics Port, an interface specification developed by Intel Corporation. AGP is based on PCI, but is designed especially for the throughput demands of 3-D graphics. Rather than using the PCI bus for graphics data, AGP introduces a dedicated point-to-point channel so that the graphics controller can directly access main memory. The AGP channel is 32 bits wide and runs at 66 MHz. It can achieve throughput up to 266Mbps.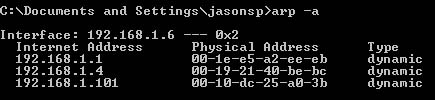
 ATA (Advanced Technology Attachment) - More frequently referred to as IDE, ATA is a connection type used in some current and most older machines to attach hard disks and optical drives to the motherboard. Variations are ATA33, ATA66, ATA100, and ATA133 with each number representing the maximum number of megabytes the host can transfer per second. Uses an older 40-pin IDE (Integrated Drive Electronics) cable for connection. To confuse matters, with the advent of Serial ATA (SATA), ATA is now referred to as Parallel ATA (PATA).
ATA (Advanced Technology Attachment) - More frequently referred to as IDE, ATA is a connection type used in some current and most older machines to attach hard disks and optical drives to the motherboard. Variations are ATA33, ATA66, ATA100, and ATA133 with each number representing the maximum number of megabytes the host can transfer per second. Uses an older 40-pin IDE (Integrated Drive Electronics) cable for connection. To confuse matters, with the advent of Serial ATA (SATA), ATA is now referred to as Parallel ATA (PATA). AUI (Attachment Unit Interface) - This 15-pin D connector is now obselete, but was used to connect devices to 10Base-5 (Thicknet) transceivers. Specifically, the AUI connector plugged into the transceiver that was attached to the thicknet backbone. It was sometimes also referred to as a DIX interface, named after DEC, Intel, and Xerox who helped create the standard.
AUI (Attachment Unit Interface) - This 15-pin D connector is now obselete, but was used to connect devices to 10Base-5 (Thicknet) transceivers. Specifically, the AUI connector plugged into the transceiver that was attached to the thicknet backbone. It was sometimes also referred to as a DIX interface, named after DEC, Intel, and Xerox who helped create the standard. CAPTCHA - Developed by Carnegie Mellon University, CAPTCHA stands for "Completely Automated Public Turing test to tell Computers and Humans Apart". This system was developed to prevent internet bots used by spammers to automatically fill out forms on web sites and submit them. On a form, CAPTCHA displays a series of distorted letters and numbers that must be correctly entered in order to submit the form. Recently, spambots have begun using character recognition software that is able to bypass this in many cases.
CAPTCHA - Developed by Carnegie Mellon University, CAPTCHA stands for "Completely Automated Public Turing test to tell Computers and Humans Apart". This system was developed to prevent internet bots used by spammers to automatically fill out forms on web sites and submit them. On a form, CAPTCHA displays a series of distorted letters and numbers that must be correctly entered in order to submit the form. Recently, spambots have begun using character recognition software that is able to bypass this in many cases. Coaxial - This cable, often referred to as "coax", is mainly known for its use with cable television systems. It was once used on early Ethernet bus networks (10Base-2), however, it has been replaced for this application by twisted pair and fiber optic cabling. More recently, this cable has proven itself useful for broadband internet connections because of its ability to transmit large amounts of data over long distances. This cable is made of a central conductive core that is wrapped in an insulator and then a second conductive layer. These three layers are then typically wrapped in an outer insulating layer.
Coaxial - This cable, often referred to as "coax", is mainly known for its use with cable television systems. It was once used on early Ethernet bus networks (10Base-2), however, it has been replaced for this application by twisted pair and fiber optic cabling. More recently, this cable has proven itself useful for broadband internet connections because of its ability to transmit large amounts of data over long distances. This cable is made of a central conductive core that is wrapped in an insulator and then a second conductive layer. These three layers are then typically wrapped in an outer insulating layer. CPU (Central Processing Unit) - A CPU, also known as a processor or microprocessor, can be thought of as the brains of a computer system and is responsible for executing software commands and performing calculation functions.
CPU (Central Processing Unit) - A CPU, also known as a processor or microprocessor, can be thought of as the brains of a computer system and is responsible for executing software commands and performing calculation functions. 
 DB Connector - Describes a series of port connectors for connecting devices to a computer. It gets its name because the connectors have a definite shape like a capital D (also could be called a trapezoid with rounded angles). Typically these come with 9, 15, 25, 50, or 68 pins and can be male or female depending on the cable's function.
DB Connector - Describes a series of port connectors for connecting devices to a computer. It gets its name because the connectors have a definite shape like a capital D (also could be called a trapezoid with rounded angles). Typically these come with 9, 15, 25, 50, or 68 pins and can be male or female depending on the cable's function. DDR SDRAM - Double-Data-Rate Synchronous Dynamic Random Access Memory is a type of memory integrated circuit used in modern computers. It achieves greater bandwidth than ordinary SDRAM by transferring data on both the rising and falling edges of the clock signal (double pumped). This effectively nearly doubles the transfer rate without increasing the frequency of the front side bus. Thus a 100 MHz DDR system has an effective clock rate of 200 MHz when compared to equivalent SDR SDRAM, the “SDR” being a retroactive designation. With data being transferred 8 bytes at a time DDR RAM gives a transfer rate of (memory bus clock rate) × 2 (for dual rate) × 8 (number of bytes transferred). Thus with a bus frequency of 100 MHz, DDR-SDRAM gives a max transfer rate of 1600 MB/s. The DDR SDRAM standard is evolving, from DDR to DDR2 to DDR-3.
DDR SDRAM - Double-Data-Rate Synchronous Dynamic Random Access Memory is a type of memory integrated circuit used in modern computers. It achieves greater bandwidth than ordinary SDRAM by transferring data on both the rising and falling edges of the clock signal (double pumped). This effectively nearly doubles the transfer rate without increasing the frequency of the front side bus. Thus a 100 MHz DDR system has an effective clock rate of 200 MHz when compared to equivalent SDR SDRAM, the “SDR” being a retroactive designation. With data being transferred 8 bytes at a time DDR RAM gives a transfer rate of (memory bus clock rate) × 2 (for dual rate) × 8 (number of bytes transferred). Thus with a bus frequency of 100 MHz, DDR-SDRAM gives a max transfer rate of 1600 MB/s. The DDR SDRAM standard is evolving, from DDR to DDR2 to DDR-3. EISA (Extended Industry Standard Architecture) - EISA is a bus standard for IBM compatible computers. It was announced in late 1988 by PC clone vendors as a counter to IBM's use of its proprietary MicroChannel Architecture (MCA) in its PS/2 series. EISA extends the ISA bus architecture to 32 bits and allows more than one CPU to share the bus. The bus mastering support is also enhanced to provide access to 4 GB of memory. Unlike MCA, EISA can accept older XT and ISA boards — the lines and slots for EISA are a superset of ISA. Although somewhat inferior to MCA, EISA was much favoured by manufacturers due to the proprietary nature of MCA, and even IBM produced some machines supporting it. It was somewhat expensive to implement (though not as much as MCA), so it never became particularly popular in desktop PCs. However, it was reasonably successful in the server market, as it was better suited to bandwidth-intensive tasks (such as disk access and networking). Most EISA cards produced were either SCSI or network cards. EISA is not commonly seen anymore.
EISA (Extended Industry Standard Architecture) - EISA is a bus standard for IBM compatible computers. It was announced in late 1988 by PC clone vendors as a counter to IBM's use of its proprietary MicroChannel Architecture (MCA) in its PS/2 series. EISA extends the ISA bus architecture to 32 bits and allows more than one CPU to share the bus. The bus mastering support is also enhanced to provide access to 4 GB of memory. Unlike MCA, EISA can accept older XT and ISA boards — the lines and slots for EISA are a superset of ISA. Although somewhat inferior to MCA, EISA was much favoured by manufacturers due to the proprietary nature of MCA, and even IBM produced some machines supporting it. It was somewhat expensive to implement (though not as much as MCA), so it never became particularly popular in desktop PCs. However, it was reasonably successful in the server market, as it was better suited to bandwidth-intensive tasks (such as disk access and networking). Most EISA cards produced were either SCSI or network cards. EISA is not commonly seen anymore.  FDDI - Stands for Fiber Distrubuted Data Interface which is a set of ANSI protocols which specifies a 100-Mbps token-passing, dual-ring LAN using fiber-optic cable. FDDI uses dual-ring architecture with traffic on each ring flowing in opposite directions (called counter-rotating). The dual rings consist of a primary and a secondary ring. During normal operation, the primary ring is used for data transmission, and the secondary ring remains idle. FDDI defines two types of optical fiber: single-mode and multimode. A mode is a ray of light that enters the fiber at a particular angle. Multimode fiber uses LED as the light-generating device, while single-mode fiber generally uses lasers. FDDI allows 2 km between stations using multimode fiber, and even longer distances using a single mode. An extension to FDDI, called FDDI-2, supports the transmission of voice and video information as well as data. Another variation of FDDI, called FDDI Full Duplex Technology (FFDT) uses the same network infrastructure but can potentially support data rates up to 200 Mbps.
FDDI - Stands for Fiber Distrubuted Data Interface which is a set of ANSI protocols which specifies a 100-Mbps token-passing, dual-ring LAN using fiber-optic cable. FDDI uses dual-ring architecture with traffic on each ring flowing in opposite directions (called counter-rotating). The dual rings consist of a primary and a secondary ring. During normal operation, the primary ring is used for data transmission, and the secondary ring remains idle. FDDI defines two types of optical fiber: single-mode and multimode. A mode is a ray of light that enters the fiber at a particular angle. Multimode fiber uses LED as the light-generating device, while single-mode fiber generally uses lasers. FDDI allows 2 km between stations using multimode fiber, and even longer distances using a single mode. An extension to FDDI, called FDDI-2, supports the transmission of voice and video information as well as data. Another variation of FDDI, called FDDI Full Duplex Technology (FFDT) uses the same network infrastructure but can potentially support data rates up to 200 Mbps.  Firewall - Either a hardware or software entity (or a combination of both) that protects a network by stopping network traffic from passing through it. In most cases, a firewall is placed on the network to allow all internal traffic to leave the network (email to the outside world, web access, etc.), but stop unwanted traffic from the outside world from entering the internal network. This is achieved by granting and denying access to various ports.
Firewall - Either a hardware or software entity (or a combination of both) that protects a network by stopping network traffic from passing through it. In most cases, a firewall is placed on the network to allow all internal traffic to leave the network (email to the outside world, web access, etc.), but stop unwanted traffic from the outside world from entering the internal network. This is achieved by granting and denying access to various ports.  Firewire (IEEE-1394) - A very fast external bus similar to USB that supports data transfer rates of up to 400 Mbps. Firewire was developed by Apple and falls under the IEEE 1394 standard. Also known as the High Performance Serial Bus, firewire can connect up to 63 devices in a tree-like daisy chain configuration. It supports plug-and-play and peer-to-peer communication between
Firewire (IEEE-1394) - A very fast external bus similar to USB that supports data transfer rates of up to 400 Mbps. Firewire was developed by Apple and falls under the IEEE 1394 standard. Also known as the High Performance Serial Bus, firewire can connect up to 63 devices in a tree-like daisy chain configuration. It supports plug-and-play and peer-to-peer communication between  Flash Drives - Flash drives offer advantages over other portable storage devices and are partially responsible for the disappearance of floppy and ZIP disk technologies. They are more compact, generally faster, hold more data, and are more reliable due to both their lack of moving parts (solid state), and their more durable design. These types of drives use the USB mass storage standard, and therefore, can be used with Linux, Mac OS X, Unix, and Windows. The drive is simply plugged into the computer's USB port and it registers as removable storage in My Computer (Windows). Newer computer systems will also allow these drives to be selected as the boot device which can be useful for storing certain utilities and troubleshooting tools. In Windows Vista, the ReadyBoost feature allows use of a flash drive to supplement system memory. At the time of this writing there are flash drives with a storage capacity of up to 64 gigabytes.
Flash Drives - Flash drives offer advantages over other portable storage devices and are partially responsible for the disappearance of floppy and ZIP disk technologies. They are more compact, generally faster, hold more data, and are more reliable due to both their lack of moving parts (solid state), and their more durable design. These types of drives use the USB mass storage standard, and therefore, can be used with Linux, Mac OS X, Unix, and Windows. The drive is simply plugged into the computer's USB port and it registers as removable storage in My Computer (Windows). Newer computer systems will also allow these drives to be selected as the boot device which can be useful for storing certain utilities and troubleshooting tools. In Windows Vista, the ReadyBoost feature allows use of a flash drive to supplement system memory. At the time of this writing there are flash drives with a storage capacity of up to 64 gigabytes.  Ghosting - Ghosting is a condition where the image prints properly, but a much lighter copy of the image also prints elsewhere. This can be due to a problem with the power outlet that is supplying power to the printer. Check the power outlet by plugging in a different printer to see if the same results occur. Ghosting can also be caused when consumable printer parts, such as the drum or imaging kit, are near the end of their life. All of the consumable parts in a printer are rated for a certain number of pages. Once a printer gets near that number, you'll need to replace those parts to eliminate ghosting.
Ghosting - Ghosting is a condition where the image prints properly, but a much lighter copy of the image also prints elsewhere. This can be due to a problem with the power outlet that is supplying power to the printer. Check the power outlet by plugging in a different printer to see if the same results occur. Ghosting can also be caused when consumable printer parts, such as the drum or imaging kit, are near the end of their life. All of the consumable parts in a printer are rated for a certain number of pages. Once a printer gets near that number, you'll need to replace those parts to eliminate ghosting. GPS (Global Positioning System) - GPS refers to satellite-based radio positioning systems that provides one's exact location anywhere on or near the surface of the Earth. The NAVSTAR system, operated by the US Department of Defense, was the first GPS system widely available to civilian users who now use it for navigation purposes. Many corporations, such as UPS, use this technology for inventory tracking. GPS is made possible by a series of at least 24 geosynchronous satellites.
GPS (Global Positioning System) - GPS refers to satellite-based radio positioning systems that provides one's exact location anywhere on or near the surface of the Earth. The NAVSTAR system, operated by the US Department of Defense, was the first GPS system widely available to civilian users who now use it for navigation purposes. Many corporations, such as UPS, use this technology for inventory tracking. GPS is made possible by a series of at least 24 geosynchronous satellites.
 Hub - A physical layer network device used to connect multiple Ethernet devices together. Active hubs act as a repeater and boost the signal in order to allow for it to travel farther, while passive hubs simply pass the signal through. Most hubs have an uplink port that allows them to connect to other hubs, a router, or other network device.
Hub - A physical layer network device used to connect multiple Ethernet devices together. Active hubs act as a repeater and boost the signal in order to allow for it to travel farther, while passive hubs simply pass the signal through. Most hubs have an uplink port that allows them to connect to other hubs, a router, or other network device.
 ISA Server (Internet Security & Acceleration Server) - ISA Server is an integrated edge security gateway produced by Microsoft that helps protect IT environments from Internet-based threats while providing users fast and secure remote access to applications and data. ISA Server is the successor to Microsoft's Proxy Server 2.0. ISA Server provides the two basic services of an enterprise firewall and a Web proxy/cache server. ISA Server's firewall screens all packet-level, circuit-level, and application-level traffic. The Web cache stores and serves all regularly accessed Web content in order to reduce network traffic and provide faster access to frequently-accessed Web pages.
ISA Server (Internet Security & Acceleration Server) - ISA Server is an integrated edge security gateway produced by Microsoft that helps protect IT environments from Internet-based threats while providing users fast and secure remote access to applications and data. ISA Server is the successor to Microsoft's Proxy Server 2.0. ISA Server provides the two basic services of an enterprise firewall and a Web proxy/cache server. ISA Server's firewall screens all packet-level, circuit-level, and application-level traffic. The Web cache stores and serves all regularly accessed Web content in order to reduce network traffic and provide faster access to frequently-accessed Web pages.  Jumpers - A metal bridge that closes an electrical circuit. Typically, a jumper consists of a plastic plug with metal contacts inside that fits over a pair of protruding pins. Jumpers are sometimes used to configure expansion boards, hard drives, and other devices. By placing a jumper plug over a different set of pins, you can change a board's parameters.
Jumpers - A metal bridge that closes an electrical circuit. Typically, a jumper consists of a plastic plug with metal contacts inside that fits over a pair of protruding pins. Jumpers are sometimes used to configure expansion boards, hard drives, and other devices. By placing a jumper plug over a different set of pins, you can change a board's parameters. KVM Switch - A Keyboard, Video, Mouse (KVM) Switch is a device that allows multiple computers to share 1 keyboard, video monitor, and mouse. A KVM switch allows the user to interact only with one computer at a time, but a series of key strokes or other method can be used to switch computers.
KVM Switch - A Keyboard, Video, Mouse (KVM) Switch is a device that allows multiple computers to share 1 keyboard, video monitor, and mouse. A KVM switch allows the user to interact only with one computer at a time, but a series of key strokes or other method can be used to switch computers. LAN (Local Area Network) - A computer network that spans a relatively small area and typically offers high-speed communications. Most LANs are confined to a single building or group of buildings. However, one LAN can be connected to other LANs over any distance via
LAN (Local Area Network) - A computer network that spans a relatively small area and typically offers high-speed communications. Most LANs are confined to a single building or group of buildings. However, one LAN can be connected to other LANs over any distance via  NIC (Network Interface Card) - A Network Interface Card is an expansion board you insert into a computer so the computer can be connected to a network. Most NICs are designed for a particular type of network, protocol and media, although some can serve multiple
NIC (Network Interface Card) - A Network Interface Card is an expansion board you insert into a computer so the computer can be connected to a network. Most NICs are designed for a particular type of network, protocol and media, although some can serve multiple  NSLOOKUP - This is a command that queries a DNS server for machine name and address information. Originally written for Unix operating systems, this command is now available on Windows and other operating systems. To use nslookup, type "nslookup" followed by an IP address, a computer name, or a domain name. NSLOOKUP will return the name, all known IP addresses and all known aliases (which are just alternate names) for the identified machine. NSLOOKUP is a useful tool for troubleshooting DNS problems.
NSLOOKUP - This is a command that queries a DNS server for machine name and address information. Originally written for Unix operating systems, this command is now available on Windows and other operating systems. To use nslookup, type "nslookup" followed by an IP address, a computer name, or a domain name. NSLOOKUP will return the name, all known IP addresses and all known aliases (which are just alternate names) for the identified machine. NSLOOKUP is a useful tool for troubleshooting DNS problems. Parallel Port - A parallel port is used to connect printers to computers. This connector stands out as the biggest connector (usually) on the back of your PC. It is usually next to the serial ports. It is a DB-25 connector on the PC and usually a Centronics 36 pin connection to the peripheral. *Warning* There are SCSI 1 connectors that look like this and will actually fit together - Doing so can potentially damage your printer or PC. Just look for the SCSI symbol to tell the difference.
Parallel Port - A parallel port is used to connect printers to computers. This connector stands out as the biggest connector (usually) on the back of your PC. It is usually next to the serial ports. It is a DB-25 connector on the PC and usually a Centronics 36 pin connection to the peripheral. *Warning* There are SCSI 1 connectors that look like this and will actually fit together - Doing so can potentially damage your printer or PC. Just look for the SCSI symbol to tell the difference. Patch Panel - A panel of network ports contained together, usually within a wiring closet, that connects incoming and outgoing lines of a LAN or other communication, electronic or electrical systems. In a LAN, the patch panel connects the network's computers to each other and to the outside lines that enable the LAN to connect to the Internet or another WAN. Connections are made with patch cables.
Patch Panel - A panel of network ports contained together, usually within a wiring closet, that connects incoming and outgoing lines of a LAN or other communication, electronic or electrical systems. In a LAN, the patch panel connects the network's computers to each other and to the outside lines that enable the LAN to connect to the Internet or another WAN. Connections are made with patch cables. PCI - Stands for Peripheral Component Interconnect and is personal computer local bus designed by Intel. It provides a high-speed connection at 33Mhz with peripherals and allows connection of seven peripheral devices. It is mostly used with Pentium computers but is processor independent and therefore able to work with other processors. Supports PnP, Burst Mode, Bus Mastering. Utilizes the host bridge to communicate with other types of expansion slots. The 32-bit version is the most common and it has displaced ISA and VESA architectures.
PCI - Stands for Peripheral Component Interconnect and is personal computer local bus designed by Intel. It provides a high-speed connection at 33Mhz with peripherals and allows connection of seven peripheral devices. It is mostly used with Pentium computers but is processor independent and therefore able to work with other processors. Supports PnP, Burst Mode, Bus Mastering. Utilizes the host bridge to communicate with other types of expansion slots. The 32-bit version is the most common and it has displaced ISA and VESA architectures. POP3 (Post Office Protocol) - POP3 is the protocol used to retrieve messages from a mail server. POP3 facilitates the downloading of messages to an email client such as Microsoft Outlook or Eudora. IMAP is an alternative to POP3 that offers more features, but currently POP3 is the most commonly used protocol for this purpose. POP3 utilizes port 110.
POP3 (Post Office Protocol) - POP3 is the protocol used to retrieve messages from a mail server. POP3 facilitates the downloading of messages to an email client such as Microsoft Outlook or Eudora. IMAP is an alternative to POP3 that offers more features, but currently POP3 is the most commonly used protocol for this purpose. POP3 utilizes port 110. Port1 - A single PC may be sending email, receiving a Telnet request, and accessing the Internet at the same time. Ports keep these "conversations" separate. Each potential type of conversation a host can have is preassigned a port number, and these port numbers allow different types of communications to take place over the same physical cable by keeping them logically separated.
Port1 - A single PC may be sending email, receiving a Telnet request, and accessing the Internet at the same time. Ports keep these "conversations" separate. Each potential type of conversation a host can have is preassigned a port number, and these port numbers allow different types of communications to take place over the same physical cable by keeping them logically separated. Power Supply - The power supply converts electricity received from a wall outlet (120V AC in the USA) into DC current amounts that are needed by the various components of a computer system.
Power Supply - The power supply converts electricity received from a wall outlet (120V AC in the USA) into DC current amounts that are needed by the various components of a computer system. QWERTY - Pronounced "kwerty", QWERTY refers to the first 6 letters in the upper left corner of an English-language keyboard. This keyboard layout was developed by Christopher Sholes in 1868. The keys were layed out in this manner to increase productivity.
QWERTY - Pronounced "kwerty", QWERTY refers to the first 6 letters in the upper left corner of an English-language keyboard. This keyboard layout was developed by Christopher Sholes in 1868. The keys were layed out in this manner to increase productivity. RDRAM - Rambus DRAM adds support for even faster bus speeds and first surfaced around the time of the Pentium IV. RDRAM uses RIMMS which require a heat spreader to be attached to the RIMM to deal with its increased heat levels. Unused slots on a RDRAM motherboard must be terminated with a CRIMM in order to function. Although it is faster than many other types of RAM, the technology never really caught on due to high prices.
RDRAM - Rambus DRAM adds support for even faster bus speeds and first surfaced around the time of the Pentium IV. RDRAM uses RIMMS which require a heat spreader to be attached to the RIMM to deal with its increased heat levels. Unused slots on a RDRAM motherboard must be terminated with a CRIMM in order to function. Although it is faster than many other types of RAM, the technology never really caught on due to high prices. RJ-11 - Short for Registered Jack-11, a four or six-wire connector used primarily to connect telephone equipment in the United States. The cable itself is called category 1 (Cat 1).
RJ-11 - Short for Registered Jack-11, a four or six-wire connector used primarily to connect telephone equipment in the United States. The cable itself is called category 1 (Cat 1). RJ-45 - Short for Registered Jack-45, it is an eight-wire connector used commonly to connect devices on Ethernet LANs. RJ-45 connectors look similar to RJ-11 connectors used for connecting telephone equipment, but they are larger.
RJ-45 - Short for Registered Jack-45, it is an eight-wire connector used commonly to connect devices on Ethernet LANs. RJ-45 connectors look similar to RJ-11 connectors used for connecting telephone equipment, but they are larger. Router - Functioning at the network later of the OSI model, a router is similar to a switch, but it can also connect different logical networks or subnets and enable traffic that is destined for the networks on the other side of the router to pass through. Routers create or maintain a table of the available routes and can be configured to use various routing protocols to determine the best route for a given data packet. Routers can connect networks that use disimilar protocols. Routers also typically provide improved security functions over a switch.
Router - Functioning at the network later of the OSI model, a router is similar to a switch, but it can also connect different logical networks or subnets and enable traffic that is destined for the networks on the other side of the router to pass through. Routers create or maintain a table of the available routes and can be configured to use various routing protocols to determine the best route for a given data packet. Routers can connect networks that use disimilar protocols. Routers also typically provide improved security functions over a switch. SCSI (Small Computer Systems Interface) - Prounounced "Scuzzy", SCSI is an alternative to the IDE interface for connecting mass storage devices. SCSI is faster than IDE, however, because of its cost SCSI devices are most commonly found in servers and high-end workstations. SCSI devices, such as hard drives, tape drives, and CD-ROM drives, plug into a SCSI controller internally or externally, and multiple devices can be configured in a chain. In order for the SCSI bus to work correctly, the last device on any SCSI chain must be terminated. Some SCSI devices are self-terminating, while others can be terminated using jumpers or a resistor that plugs into the end of the cable or device. Each device on a SCSI chain must receive its own SCSI ID including the controller which is usually preset to ID 7. Newer SCSI standards support up to 16 devices in a chain.
SCSI (Small Computer Systems Interface) - Prounounced "Scuzzy", SCSI is an alternative to the IDE interface for connecting mass storage devices. SCSI is faster than IDE, however, because of its cost SCSI devices are most commonly found in servers and high-end workstations. SCSI devices, such as hard drives, tape drives, and CD-ROM drives, plug into a SCSI controller internally or externally, and multiple devices can be configured in a chain. In order for the SCSI bus to work correctly, the last device on any SCSI chain must be terminated. Some SCSI devices are self-terminating, while others can be terminated using jumpers or a resistor that plugs into the end of the cable or device. Each device on a SCSI chain must receive its own SCSI ID including the controller which is usually preset to ID 7. Newer SCSI standards support up to 16 devices in a chain. Secure Digital Cards - Secure Digital (SD) cards are the most commonly used format today after displacing a similar type by SmartMedia. SD cards come in 2 types: SD and SDIO. Both are identical looking so you need to check with the manual or manufacturer of your device to find which to use. SD cards are smaller than CompactFlash, but come in 2 even smaller sizes: MiniSD and MicroSD are smaller versions that are commonly used in cell phones.
Secure Digital Cards - Secure Digital (SD) cards are the most commonly used format today after displacing a similar type by SmartMedia. SD cards come in 2 types: SD and SDIO. Both are identical looking so you need to check with the manual or manufacturer of your device to find which to use. SD cards are smaller than CompactFlash, but come in 2 even smaller sizes: MiniSD and MicroSD are smaller versions that are commonly used in cell phones. Smart Card - The term smart card has been used to describe a class of credit card-sized devices with varying capabilities, however, they are most commonly used for identification, building entry, and financial transactions. The card is typically inserted into a reader device which reads the contents of the ICC chip in the card. It is the ICC (Integrated Circuit Card) that is of most interest to the personal computer because it is able to perform more sophisticated operations such as digital signature and key exchange. Newer operating systems are supporting smart card authentication.
Smart Card - The term smart card has been used to describe a class of credit card-sized devices with varying capabilities, however, they are most commonly used for identification, building entry, and financial transactions. The card is typically inserted into a reader device which reads the contents of the ICC chip in the card. It is the ICC (Integrated Circuit Card) that is of most interest to the personal computer because it is able to perform more sophisticated operations such as digital signature and key exchange. Newer operating systems are supporting smart card authentication.  STP1 (Shielded Twisted Pair) - This type of cable is the same as unshielded twisted pair (UTP), except that it has shielding around it to provide more protection against electromagnetic interference (EMI).
STP1 (Shielded Twisted Pair) - This type of cable is the same as unshielded twisted pair (UTP), except that it has shielding around it to provide more protection against electromagnetic interference (EMI). Subnet - A subnet is a logical grouping of connected network devices. Network designers use subnets as a way to divide networks into logical segments for greater ease of administration, improved security, and better performance. In IP networking, nodes on a subnet share a contiguous range of IP address numbers. A number called a subnet mask blocks out a portion of an IP address and is used to differentiate between the host ID and network ID.
Subnet - A subnet is a logical grouping of connected network devices. Network designers use subnets as a way to divide networks into logical segments for greater ease of administration, improved security, and better performance. In IP networking, nodes on a subnet share a contiguous range of IP address numbers. A number called a subnet mask blocks out a portion of an IP address and is used to differentiate between the host ID and network ID. Switch - A switch is a network device that filters and forwards packets between LAN segments and ensures that data goes straight from its origin to its proper destination. Switches remember the address of every node on the network, and anticipate where data needs to go. It only operates with the computers on the same LAN. This reduces competition for bandwidth between devices on the network.
Switch - A switch is a network device that filters and forwards packets between LAN segments and ensures that data goes straight from its origin to its proper destination. Switches remember the address of every node on the network, and anticipate where data needs to go. It only operates with the computers on the same LAN. This reduces competition for bandwidth between devices on the network.
 URL (Uniform Resource Locator) - As the name indicates, a URL is an address used to give the location of a resource on the web. The first part is the ‘service descriptor’ which identifies the protocol being used (in the diagram it is HTTP). The ‘//’ indicates the start of path (the root directory) which is followed by the domain name. The remainder of the address is the directory path on the server that specifies the location of the file to be fetched. You may have noticed that when you visit a domain, the complete path is not displayed. For example, if you visit our home page at http://www.mcmcse.com, there is no file specified after the domain name.
URL (Uniform Resource Locator) - As the name indicates, a URL is an address used to give the location of a resource on the web. The first part is the ‘service descriptor’ which identifies the protocol being used (in the diagram it is HTTP). The ‘//’ indicates the start of path (the root directory) which is followed by the domain name. The remainder of the address is the directory path on the server that specifies the location of the file to be fetched. You may have noticed that when you visit a domain, the complete path is not displayed. For example, if you visit our home page at http://www.mcmcse.com, there is no file specified after the domain name. USB (Universal Serial Bus) - A plug-and-play interface between a computer and peripherals (such as keyboards, scanners, printers, digital cameras, etc). In some situations, it can also be used to network 2
USB (Universal Serial Bus) - A plug-and-play interface between a computer and peripherals (such as keyboards, scanners, printers, digital cameras, etc). In some situations, it can also be used to network 2  UTP (Unshielded Twisted Pair) - It is a cable type that consists of two or more insulated conductors in which each pair of conductors are twisted around each other. Category 1 UTP cables are used for telephony connections. Category 3 and higher are used for Ethernet LAN connections. UTP is inexpensive and easy to work with.
UTP (Unshielded Twisted Pair) - It is a cable type that consists of two or more insulated conductors in which each pair of conductors are twisted around each other. Category 1 UTP cables are used for telephony connections. Category 3 and higher are used for Ethernet LAN connections. UTP is inexpensive and easy to work with. VLAN (Virtual Local Area Network) - A VLAN is a logical grouping of devices or users. These devices or users can be grouped by function, department application and so on, regardless of their physical segment location. VLANs create separate broadcast domains in a switched network. Frame tagging at layer 2 does this. Frame tagging is a gaining recognition as the standard for implementing VLANs, and is recognized by IEEE 802.1q. Frame tagging uniquely assigns a VLAN ID to each frame. This identifier is understood and examined by each switch prior to any broadcasts or transmissions to other switches, routers, and end-stations devices.
VLAN (Virtual Local Area Network) - A VLAN is a logical grouping of devices or users. These devices or users can be grouped by function, department application and so on, regardless of their physical segment location. VLANs create separate broadcast domains in a switched network. Frame tagging at layer 2 does this. Frame tagging is a gaining recognition as the standard for implementing VLANs, and is recognized by IEEE 802.1q. Frame tagging uniquely assigns a VLAN ID to each frame. This identifier is understood and examined by each switch prior to any broadcasts or transmissions to other switches, routers, and end-stations devices. VPN (Virtual Private Network) - A VPN is a network that uses a public telecommunication infrastructure, such as the Internet, to provide remote offices or individual users with secure access to their organization's network. A VPN works by using the shared public infrastructure while maintaining privacy through security procedures and tunneling protocols such as the Layer Two Tunneling Protocol (L2TP) or PPTP. In effect, the protocols, by encrypting data at the sending end and decrypting it at the receiving end, send the data through a "tunnel" that cannot be "entered" by data that is not properly encrypted.
VPN (Virtual Private Network) - A VPN is a network that uses a public telecommunication infrastructure, such as the Internet, to provide remote offices or individual users with secure access to their organization's network. A VPN works by using the shared public infrastructure while maintaining privacy through security procedures and tunneling protocols such as the Layer Two Tunneling Protocol (L2TP) or PPTP. In effect, the protocols, by encrypting data at the sending end and decrypting it at the receiving end, send the data through a "tunnel" that cannot be "entered" by data that is not properly encrypted. WAN (Wide Area Network) - A computer network that spans a relatively large geographical area. Typically, a WAN consists of two or more local-area
WAN (Wide Area Network) - A computer network that spans a relatively large geographical area. Typically, a WAN consists of two or more local-area 
 WLAN (Wireless Local Area Network) - A WLAN is local area network available through a wireless connection using the 802.11 family of standards. The wireless connections utilize spread-spectrum technology based on radio waves to enable communication between devices in a limited area.
WLAN (Wireless Local Area Network) - A WLAN is local area network available through a wireless connection using the 802.11 family of standards. The wireless connections utilize spread-spectrum technology based on radio waves to enable communication between devices in a limited area. ZIF (Zero Insertion Force) - A ZIF Socket is The ZIF socket has a small lever on the side of it which is lifted to release the CPU or allow one to be inserted. Once the CPU is in place, the lever is pushed down and the electrical contacts grip the pins on the CPU clamping it into place. This socket type was invented to prevent damage to the CPU caused by the force required to press the CPU into place. Previous designs also had a risk of bending the pins on the
ZIF (Zero Insertion Force) - A ZIF Socket is The ZIF socket has a small lever on the side of it which is lifted to release the CPU or allow one to be inserted. Once the CPU is in place, the lever is pushed down and the electrical contacts grip the pins on the CPU clamping it into place. This socket type was invented to prevent damage to the CPU caused by the force required to press the CPU into place. Previous designs also had a risk of bending the pins on the  ZIP Drive - Introduced by Iomega in 1994, ZIP drives are internal or external storage devices that used removable ZIP disks to store data. Later versions of ZIP disks could store up to 750mb of data. Internal ZIP drives came with either an IDE or SCSI interface, while external drives came with either a parallel, SCSI, or USB (later years) interface. The external versions were popular due to their portability. The original Zip drive had a data transfer rate of about 1 megabyte/second and a seek time of 28 milliseconds on average, compared to a standard 1.44 MB floppy's 500 kbit/s (62.5 kB/s) transfer rate and several-hundred millisecond average seek time. The ZIP drive's popularity was fleeting as larger capacity options such as CD/DVD burners, flash drives, and other technologies have made them almost obselete.
ZIP Drive - Introduced by Iomega in 1994, ZIP drives are internal or external storage devices that used removable ZIP disks to store data. Later versions of ZIP disks could store up to 750mb of data. Internal ZIP drives came with either an IDE or SCSI interface, while external drives came with either a parallel, SCSI, or USB (later years) interface. The external versions were popular due to their portability. The original Zip drive had a data transfer rate of about 1 megabyte/second and a seek time of 28 milliseconds on average, compared to a standard 1.44 MB floppy's 500 kbit/s (62.5 kB/s) transfer rate and several-hundred millisecond average seek time. The ZIP drive's popularity was fleeting as larger capacity options such as CD/DVD burners, flash drives, and other technologies have made them almost obselete.